Security researchers found a new type of web attack last month named CPDoS (Cache-Poisoned Denial-of-Service), that can poison content delivery networks (CDNs) into caching and then serving error pages instead of legitimate websites.
Cache-Poisoned Denial-of-Service (CPDoS) is a new class of web cache poisoning attacks aimed at disabling web resources and websites. CPDoS enables a malicious client to block any web resource that is distributed via Content Distribution Networks (CDNs) or hosted on proxy caches. As per the researchers a single crafted request is sufficient to restrain all subsequent requests from accessing the targeted contents
These types of attacks target two components of the modern web -- (1) web servers and (2) content delivery networks.
Web servers store the original website and its content, while CDNs store a cached copy of the website that is only refreshed at certain time intervals.
CDNs are used to reduce the load on web servers. A web server is used to compute the same user request over and over again but a CDN provides some of the incoming users with a copy of the website, until the CDN refreshes itself with a new version.
Three types of CPDoS attacks exist right now, namely:
- HTTP Header Oversize (HHO)
- HTTP Meta Character (HMC)
- HTTP Method Override (HMO)
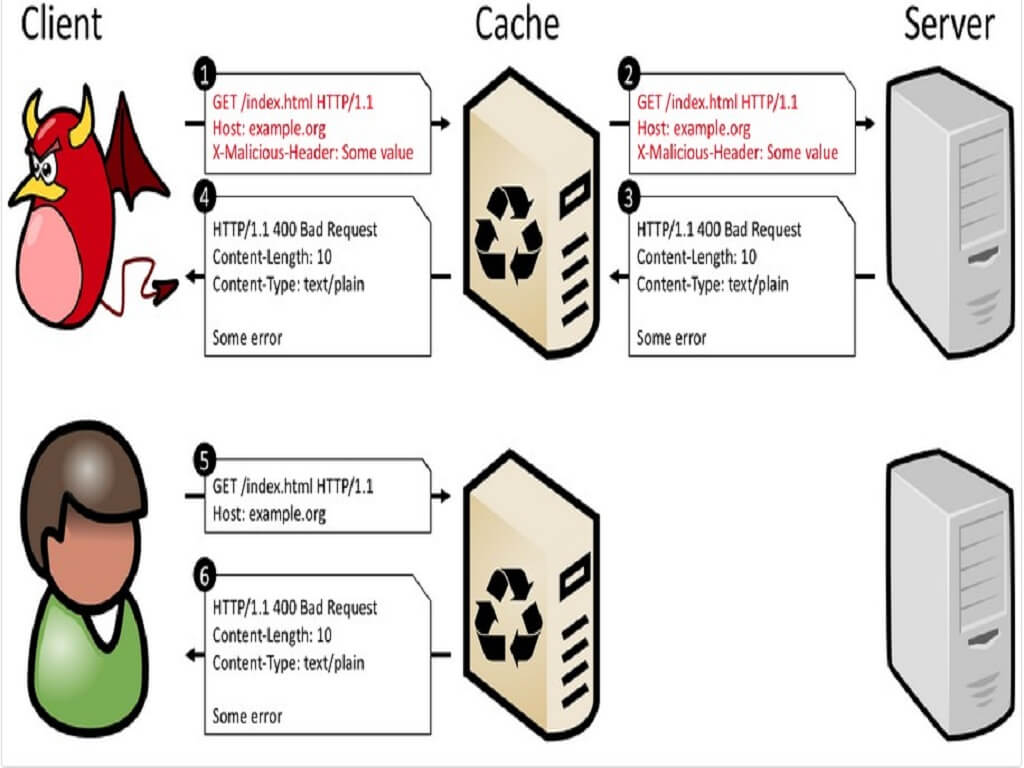
The basic attack flow of CPDoS is described below:
- An attacker sends a simple HTTP request containing a malicious header targeting a victim resource provided by some web server. The request is processed by the intermediate cache, while the malicious header remains unobtrusive.
- The cache forwards the request to the origin server as it does not store a fresh copy of the targeted resource. At the origin server, the request processing provokes an error due to the malicious header it contains.
- As a consequence, the origin server returns an error page which gets stored by the cache instead of the requested resource.
- The attacker knows that the attack was successful when she retrieved an error page in response.
- Legitimate users trying to obtain the target resource with subsequent requests...
- ...will get the cached error page instead of the original content.
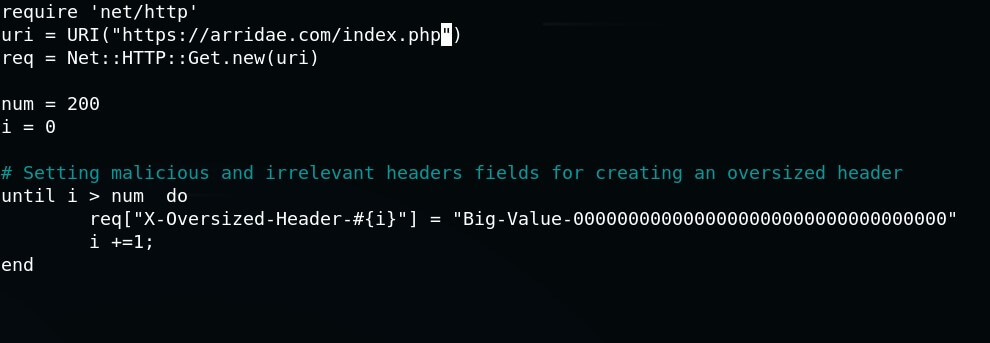
HTTP HEADER OVERSIZE (HHO) Attacks
In the case of HHO CPDoS attacks, a web application uses a cache that accepts a larger header size limit than the origin server. In order to disrupt the web application, a malicious client sends a HTTP GET request including a header larger than the size supported by the origin server but smaller than the size supported by the cache. An attacker can conduct the attack in 2 ways. First, s/he crafts a request header with many malicious headers as shown in the following Ruby code snippet. The other option is to include one single header with an oversized key or value.
HTTP Meta Character (HMC) Attacks
These attack works similar to the HHO CPDoS, here the attacker tries to bypass a cache with a request header containing a harmful meta character instead of sending an oversized header. These meta characters can be, e.g., control characters such as line break/carriage return (\n), line feed (\r) or bell (\a).
HTTP Method Override (HMO) Attacks
The HTTP standard provides several HTTP methods for web servers and clients for performing transactions on the web. GET, POST, DELETE and PUT are arguably the most used HTTP methods in web applications and REST-based web services. Many intermediate systems such as proxies, load balancers, caches, and firewalls, however, do only support GET and POST such that HTTP request methods such as DELETE and PUT are simply blocked.
Many REST-based APIs or web frameworks such as the Play Framework 1, provide headers such as X-HTTP-Method-Override, X-HTTP-Method or X-Method-Override to overcome the HTTP Method restrictions. Once the request reaches the server, the header instructs the web application to override the HTTP method in the request line with the one in the corresponding header value.
The following code snippet explains the scenario:
POST /blog/webcache.php HTTP/1.1 Host: arridae.com X-HTTP-Method-Override: DELETE HTTP/1.1 200 OK Content-Type: text/plain Content-Length: 62
Resource has been successfully removed with the DELETE method.
The researchers managed to carry out widespread cache poisoning attacks against a test website hosted on the network of several CDN providers. The researchers carried out these attacks for a shorter duration but, such attacks can create prolonged downtime for legitimate sites, incurring financial losses to the website's owner.
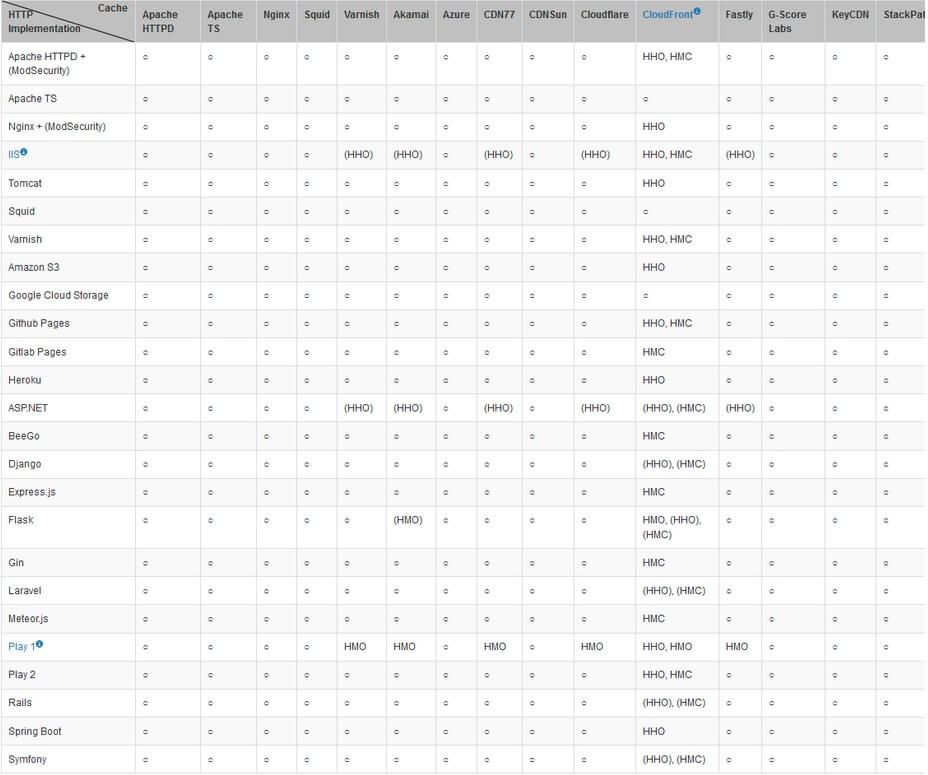
As per the researchers, the CPDoS attacks impact the CDNs in the below image