What We Offer
Check out our services
Network Pen Testing
Infrastructure vulnerabilities are mainly instigating through poor configuration or inadequate patching policies or processes.
Web Application Pen Testing
To evaluate the security of a system by methodically validating and verifying the effectiveness of application security controls.
Mobile Pen Testing
Mobile penetration testing will identify any vulnerabilities within the mobile infrastructure of your business.
Cloud Pen Testing
Cloud security is essential to assess the security of your operating systems and applications running on cloud.
RedTeam Assessment
Red teaming activities comprises of different type of penetration testing including the physical data theft to test the defense capabilities of any organization.
Wireless Pen Testing
Wi-Fi technologies pose unique threats because their signals propagate outside physical boundaries and are difficult to control.
IOT Pen Testing
The IoT also opens up companies all over the world to more security threats. Then we have the issue of privacy and data sharing.
Infrastructure Assessment
An Infrastructure Assessment is an opportunity to get a complete diagnosis of what is happening in your current environment.
Source Code Review
A Source Code review service discovers hidden vulnerabilities, design flaws, and verifies if key security controls are implemented.
Why Arridae?
Take advantage of Arridae’s extensive security expertise to enhance your existing security program. We can customize any of our services to meet your organization's needs and requirements.


All we do is Security | Offensive where we penetrate | Defensive where we protect | Investigative where we investigate | With expertise on all 3 angles it's impossible to overlook security.
Expert Team
Our team comprises of expert who possess many unique certifications and have well versed experience in the field of cyber security.
Core Solution
Our experts cover a lot of ground, and include many measures—from regular security testing and code reviews to creating security architecture and threat models—to keep a network locked down and safe from a holistic standpoint.
Remediation
Available onsite and offsite remediation support
How we deal with cyber security ?
Security is of prime importance off late.
It is often misunderstood that, if there is good protection on the surface , attacks cannot occur.
But this ain't true, because attacks can occur at various levels/components.
Arridae's expertise covers all aspects of security weaknesses in the chain namely...People, Process and Technology.
Arridae uses the sharpest knife there is in order to pierce it first then add kevlar to ensure damage does not reoccur.

IDENTIFY
Getting into the head of attacker is the best way to get ahead of threats. Arridae can help you to identify, monitor and detect the threat and to fix them on immediate basis. We prepare you for both the likely and the unexpected.

UNDERSTAND
We provide fast and accurate detection and protection against known and unknown threats. Like traditional security solutions cannot provide you with advanced persistent threat protection you need to keep your critical data safe.

RESOLVE
We detect and respond to the attacks in an expedient, effective manner. As soon as a breach is suspected we equip you with what you need to know.
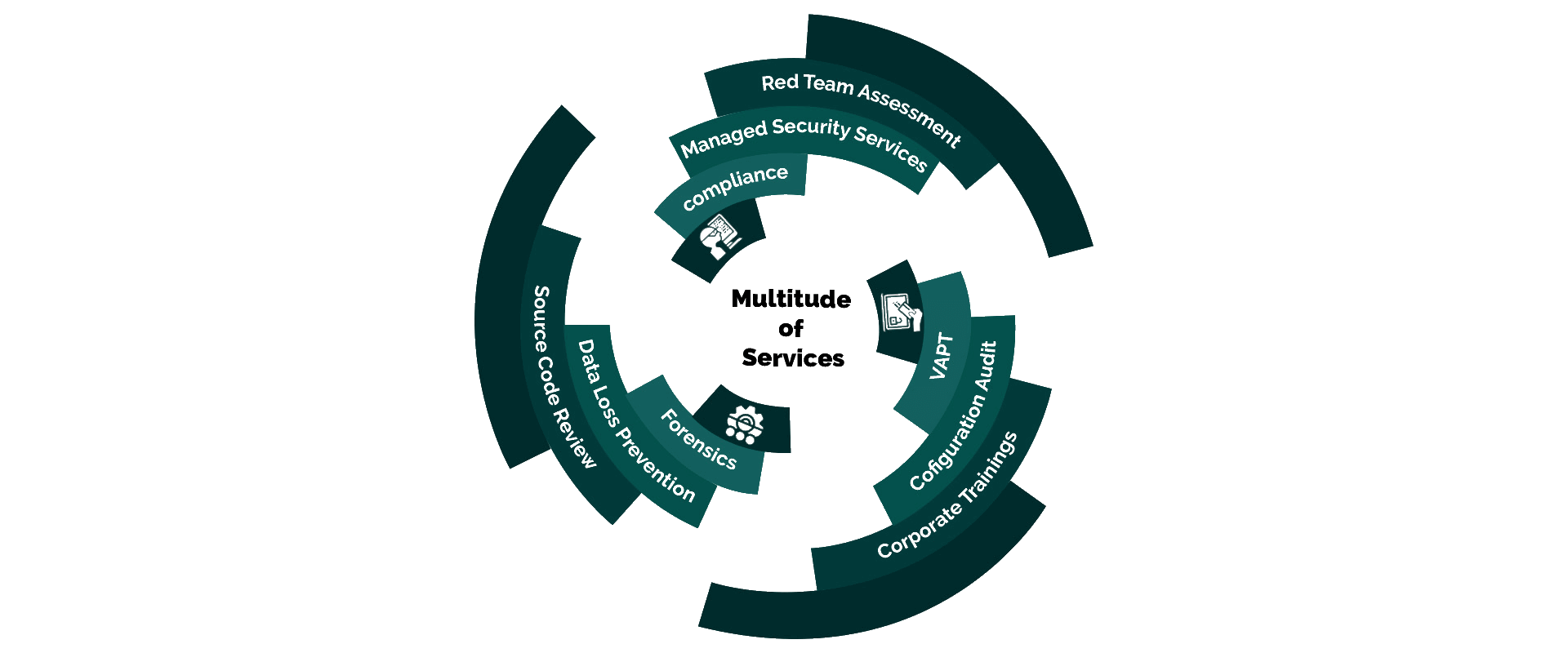

Some of Our Other Services
- All
- INVESTIGATIVE
- DEFENSIVE
Our Clients