Before we have a look at Docker, we need to understand how virtual machines work.
Virtual Machines
VMs were designed by running software on top of physical servers to emulate a particular hardware system. A hypervisor, or a virtual machine monitor, is software, firmware, or hardware that creates and runs VMs. Hypervisor sits between the hardware and the virtual machine and is necessary to virtualize the server.
Within each virtual machine runs a unique guest operating system. VMs with different operating systems can run on the same physical server—a Windows VM can sit alongside a Linux VM, and so on. Each VM has its own binaries, libraries, and applications that it services, and the VM may be many vary in size.
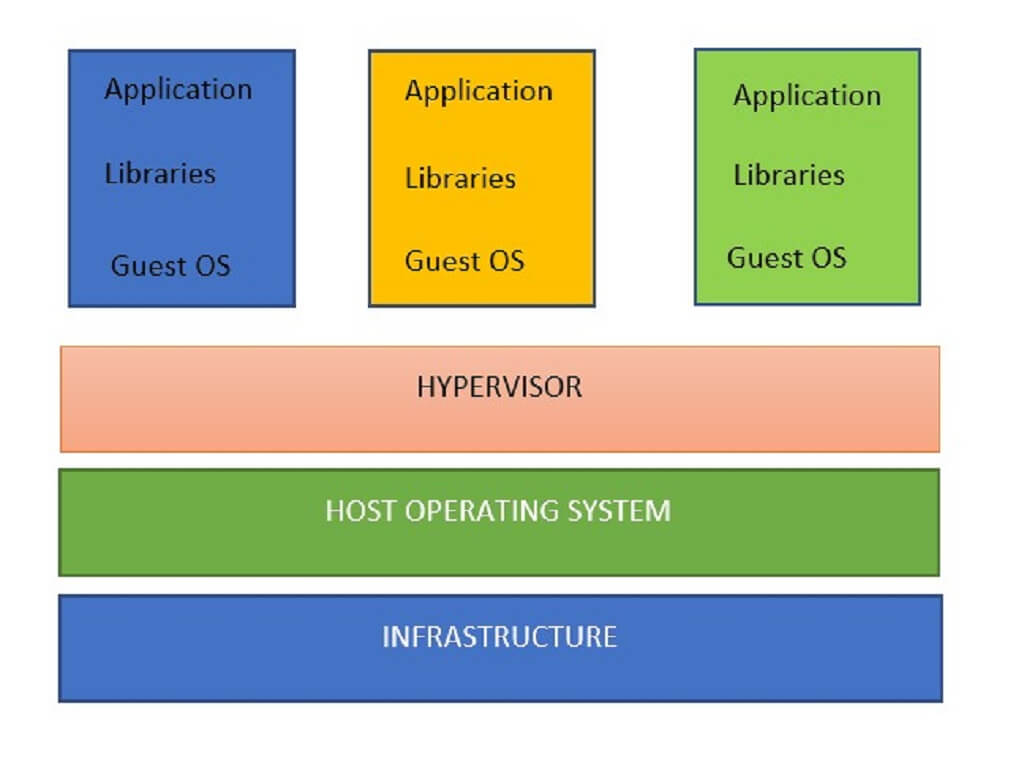
Virtual Machine Setup
Docker
Docker is container-based technology and containers use space of the operating system. At the low level, a container is just a set of processes that are isolated from the rest of the system, running from a distinct image that provides all files necessary to support the processes. It is built for running applications. In Docker, the containers running share the host OS kernel.
Containers sit on top of a physical server and its host OS—for example, Linux or Windows. Each container shares the host OS kernel and, usually, the binaries and libraries, too. Shared components are read-only. Containers are thus exceptionally “light”—they are only megabytes in size and take just seconds to start, versus gigabytes and minutes for a VM.
A Docker is made up of the following components.
- Infrastructure
- Operating System
- Docker Daemon
- Binaries and Libraries
- Applications
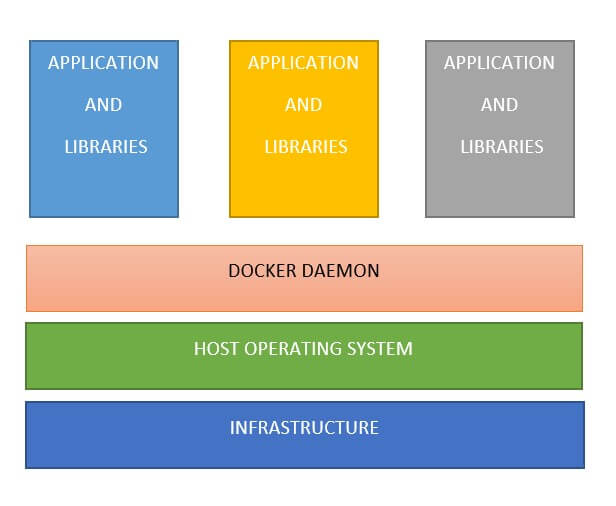
Docker Setup
Docker needs some type of infrastructure to run them, this could be a laptop or a server somewhere out there in the cloud.
Then, we have our host operating system. All major distributions of Linux are supported and there are ways to run Docker on MacOS and Windows too.
The Docker daemon is a service that runs in the background on your host operating system and manages everything required to run and interact with Docker containers.
Next comes binaries and libraries. Instead of them being ran on a guest operating system, they get built into special packages called Docker images. Then the Docker daemon runs those images.
Each application would end up residing in its own Docker image and will be managed independently by the Docker daemon. Typically each application and its library dependencies get packed into the same Docker image. As you can see, each application is still isolated.
Docker can be used to build and configure an environment by adding the tools we require and launch a container. We can also use a lightweight image to add the tools we need, and as containers don’t create disks or have to virtualise the hardware. This process allows us to have a self-contained testing environment for each test, where any processes, installs and so on are all local to that container and don’t pollute your host OS. Any data is saved in the shared volume and can be used by tools on the host, and we can still have connections back to the container for webservers, remote shells and similar.
Various useful tools for Penetration testing have been hosted officially like Amass, GoBuster on docker and there are many tools like Nmap and Wireshark are hosted for public usage by users. They do not need dependencies to run and use them this comes handy when you need those tools but cannot install them in your system. Docker Hub provides a store-like website where we can search and download images to use.
Installing Docker in Kali
Run the following commands in your terminal
sudo apt-get update sudo apt-get upgrade sudo apt-get install apt-transport-https ca-certificates curl gnupg2 software-properties-common curl -fsSL https://download.docker.com/linux/debian/gpg | sudo apt-key add - sudo apt-key fingerprint 0EBFCD88 echo 'deb [arch=amd64] https://download.docker.com/linux/debian buster stable' > /etc/apt/sources.list.d/docker.list sudo apt-get update sudo apt-get install docker-ce docker-ce-cli containerd.io -y
Intentionally vulnerable applications hosted on docker
- DVWA - docker pull citizenstig/dvwa
- NodeGOAT- docker-compose build && docker-compose up
- WebGOAT- - docker pull webgoat/webgoat-8.0 # for 8.0 version
- Vulnerability as a service: Shellshock - docker pull hmlio/vaas-cve-2014-6271
Docker Containers of Penetration Testing Distributions and Tools
Official Kali Linux - docker pull kalilinux/kali-linux-docker.
Official OWASP ZAP - docker pull owasp/zap2docker-stable.
Official WPScan - docker pull wpscanteam/wpscan.
Security Ninjas - docker pull opendns/security-ninjas.
docker-metasploit - docker pull phocean/msf





