However, the process for hacking any smart lock is the same so you can take these methods and apply them to any smart lock you like. The idea of the Smart Lock is that it can be remotely locked and unlocked using a mobile device. This become problematic because software can always be hacked and as you will see we hacked this one. The Smart Lock works with both iOS and Android operating systems.
Furthermore, the lock allows an individual to give a temporary authorization to a different phone in order for them to control the locking and unlocking of this device. The functionality also permits one to grant permanent access to another phone with the software installed. The fatal flaw of a system that is not close looped.
The Smart Lock security features were put to the test and the results are not so hot. This lock has a whole host of vulnerabilities which make it highly susceptible to being hacked. The fatal flaw is the functionality that allows one to add other authorized un-lockers. What has been found is that a hacker can easily add themselves as a guest to any lock that happens to be nearby.
HOW TO HACK A SMART LOCK
To start with, make backups of the app in random states. This is to say, different random configurations and stages of use including app states and user settings.
Going to make these four different application backups to start with:
Use cases of SSH Tunnelling (also called as SSH Port Forwarding)
- WHEN APP IS FIRST INSTALLED
- WHEN LOCK HAS BEEN PURVEYED BY THE APP
- AFTER MANY LOCK & UNLOCK COMMANDS HAVE BEEN ISSUED
- AFTER ADDITIONAL USERS HAVE BEEN ADDED TO TEST LOCK
Now, take a look at the files stored locally. This reveals that the config data is encrypted, but not so fast. There is a big ole log file that contains highly sensitive data. After analysing the source code, you can see that the code shows the encryption key that is hard coded in for all local data:
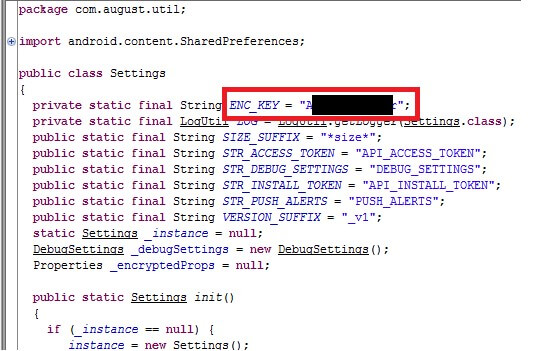
This shows the encryption key hard coded in the source file
Now that we can see what is going on with the encryption, let’s take a slightly closer look. After looking at it for a while, you can see that the routine of this encryption key dictates the cipher being used is AES and ECB. That information was then used to un-encrypt all contents located on the local host file assortment. The files accessed here have the lock UUID, username, phone number and more key identification markers. This data is also accessible in the log file first created by the application before even looking into the crypt key.
CRACKING THE API
Now that we have a solid grasp on the app in general and how it functions on the backend, we move to the API. The goal here is to look out for all the digital communication that the app has with the servers owned by Smart Locks. The app itself uses a security cert so we can’t just easily take a quick look at it. For this, we have to:
- DE-COMPILE THE ENTIRE SMART LOCK APP TO. SMALI
- REMOVE CERTIFICATE CODE FOR VALIDATION
- RECOMPILE THE ENTIRE APP
- SIGN SECURITY CERT
- RE-INSTALL APPLICATION IN THE NEWLY MODED FORM
Most of the end parts of the Smart lock API didn’t allow us to find anything too significant –there was one that did not validate that the user pressing lock/unlock are actually the owner of the lock. Behold, this is the vulnerability that we need to hack a Smart Lock. This API endpoint that is weak and vulnerable is the one that allows the owner of the smart lock to add a guest to the lock. In finding this, it means that any hacker can create an API request to add their user as a guest to any lock nearby with the correct UUID of the lock which can easily be found in the plain text log file that we found up above.
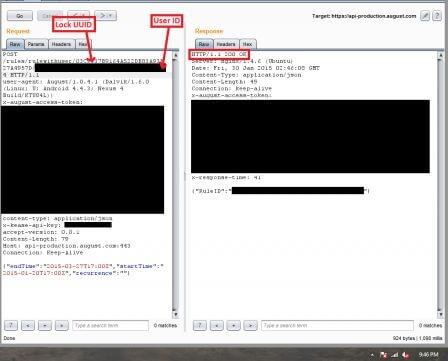
Screenshot of the API call to add guest
Now that the Smart Lock has been hacked, let’s review the conditions in which need to be present in order to crack this digital lock. For the hacker to crack this lock there are two things needed: UUID of the lock, UID of hacker. The UID can be found using a few different methods:
METHOD 1: UN-ENCRYPT LOCAL STORAGE ON HACKERS MOBILE PHONE
METHOD 2: INTERCEPT API CALL ON HACKER’S MOBILE PHONE
METHOD 3: INSPECT THE LOCAL PLAIN TEXT LOG FILE THAT WE FOUND EARLIER
The UUID of a Smart Lock can be found by simply walking up to one and using the app to scan for locks that are nearby. The mobile phone will find all that are in range. Once it does, the app will write the UUID of the locks that were discovered in the plain text log file on the mobile phone. Now that you have the UUID of the lock, you can add yourself as a guest using the Moded App that we created above and unlock the door immediately.





