LoRa was first developed and launched by Semtech Corporation in 2015. LoRa is a 'Long Range' low power wireless standard intended for providing a cellular style low data rate communications network.
LoRa uses license-free radio frequency bands like 433 MHz, 868 MHz (Europe) and 915 MHz (North America). It enables long-range transmissions (10km+ in rural and up to 2km in urban), while keeping power consumption extremely low (sub uA). The technology is presented in two parts: LoRa, the physical layer and LoRaWAN (Long Range Wide Area Network), the upper layers.
Network architecture of LoRa
A LoRa network consists of several elements:
- End points: These are the elements of the LoRa network where the sensing or control is undertaken. They are commonly located at a remote area.
- LoRa gateway: The gateway receives the communication messages from the LoRa endpoints and then transfers them onto the backend system. The backend system can be Ethernet, cellular or any other telecommunications link wired or wireless. The gateways are connected to the network server using standard IP connections. On this way the data uses a standard protocol, but can be connected to any telecommunications network, whether public or private. In view of the similarity of a LoRa network to that of a cellular one, LoRaWAN gateways may often be co-located with a cellular base station. In this way they are able to use spare capacity on the backend network.
- LoRa Network Server: The server manages the network and its function is, to eliminate duplicate packets, schedules acknowledgement, and adapts data rates. In view of the way in which it can be deployed and connected, makes it very easy to deploy a LoRa network.
- Remote computer: a remote computer is used to control the actions of the endpoints or collect data from them.
The nodes in the network are typically in a star-of-stars topology with gateways forming a transparent bridge. These relay messages between end-devices and a central network server in the backend.
Communication between end point nodes is generally bi-directional, but it is also possible to support multicast operation, and this is useful for features such as software upgrades and the like or other mass distribution messages.
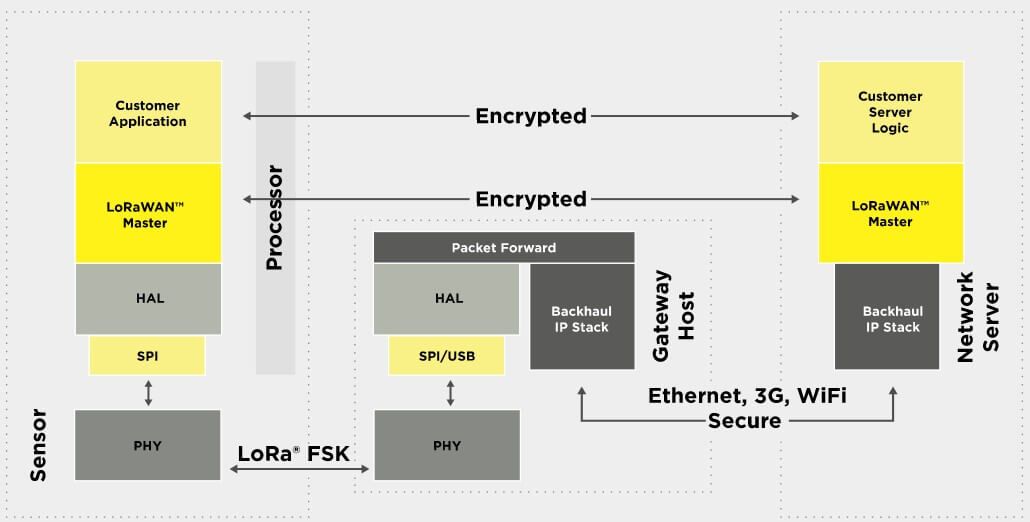
Architecture of LoRa
Modulation Technique
LoRa is based on chirp spread spectrum modulation. Chirp spread spectrum (CSS) has been used in military and space communication for decades due to the long communication distances that can be achieved and robustness to interference.
Chirp stands for 'Compressed High Intensity Radar Pulse'. It is a signal which frequency either increase or decrease with time. It is very common is sonar and radar. It is also used in spread spectrum.
Chirp Spread Spectrum:
Chirp Spread Spectrum was developed for radar applications. Chirp signals have constant amplitude and pass the whole bandwidth in a linear or non-linear way from one end to another end in a certain time. Chirp spread spectrum uses complete bandwidth to transmit signals. If the frequency changes from lowest to highest, it is call up-chirp and if the frequency changes from highest to lowest, we call it down-chirp.
In this modulation technique, spreading of spectrum is obtained by generation of a chirp signal which varies continuously in frequency. Due to this timing offset and frequency offset are equivalent between the LoRa transmitter and receiver parts. This will make receiver design very simple due to avoidance of complex algorithms. Moreover, frequency bandwidth of chirp is equivalent to spectral bandwidth of the LoRa modulated signal.
What Is LoRaWAN?
LoRaWAN is the protocol stack on top of LoRa. It is a media access control (MAC) layer protocol, acting as a network managing protocol for LPWAN. It is responsible for routing between gateways and end-nodes. Version 1.0 of the LoRaWAN specification was introduced in June 2015. Ever since it has been maintained by the LoRa Alliance.
LoRaWAN defines the communication protocol and system architecture for the network, while the LoRa physical layer enables the long-range communication link. LoRaWAN is also responsible for managing the communication frequencies, data rate, and power for all devices. Devices transmit asynchronously; when they have data to send. Data transmitted by an end-node device is received by multiple gateways, which forward the data packets to a centralized network server. The network server filters duplicate packets, performs security checks, and manages the network. Data is then forwarded to application servers.
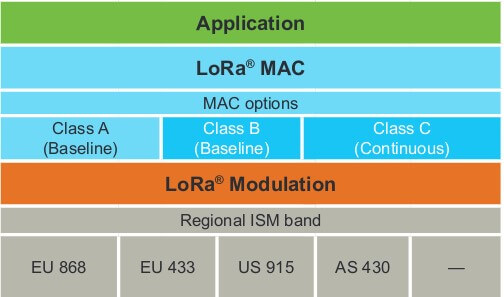
LoRaWAN Protocol Layer
LoRaWAN specification varies slightly from region to region based on the different regional spectrum allocations and regulatory requirements. Only the LoRaWAN specification for Europe and North America are defined, but other regions are still being defined by the technical committee.
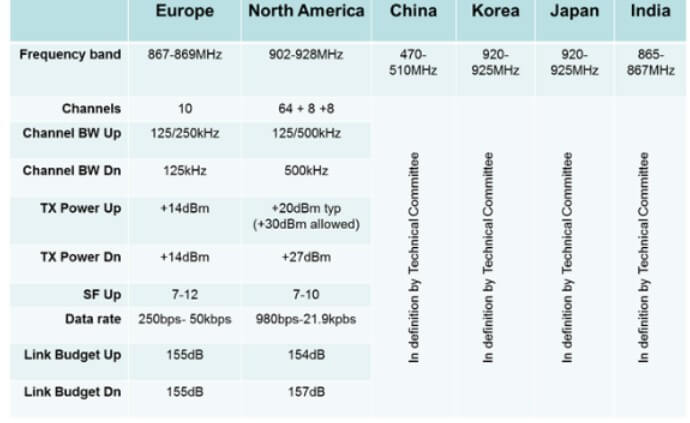
LoRaWAN Specification
Advantages of LoRa
Long Range
-It has Deep indoor coverage and range may vary from 2km+ to 10km + based on the population density.
Max Lifetime
-It has a lifetime of 10-20years
Low Cost
-It requires Minimal infrastructure and end nodes are of Low cost
Disadvantages of LoRa
Low Data Rate
- It is designed for devices that can tolerate large delays while data transmission.
Security in LoRaWAN
The LoRaWAN specification defines two layers of cryptography:
- A unique 128-bit Network Session Key shared between the end-device and network server
- A unique 128-bit Application Session Key (AppSKey) shared end-to-end at the application level
AES algorithms are used to provide authentication and integrity of packets to the network server and end-to-end encryption to the application server. By providing these two levels, it becomes possible to implement ‘multi-tenant’ shared networks without the network operator having visibility of the user’s payload data.
The keys can be Activated by Personalisation (ABP) on the production line or during commissioning, or can be Over-The-Air Activated (OTAA) in the field. OTAA allows devices to be re-keyed if necessary.





