OAuth is an open standard for access delegation, commonly used as a way for Internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Facebook, Microsoft and Twitter to permit the users to share information about their accounts with third party applications or websites.
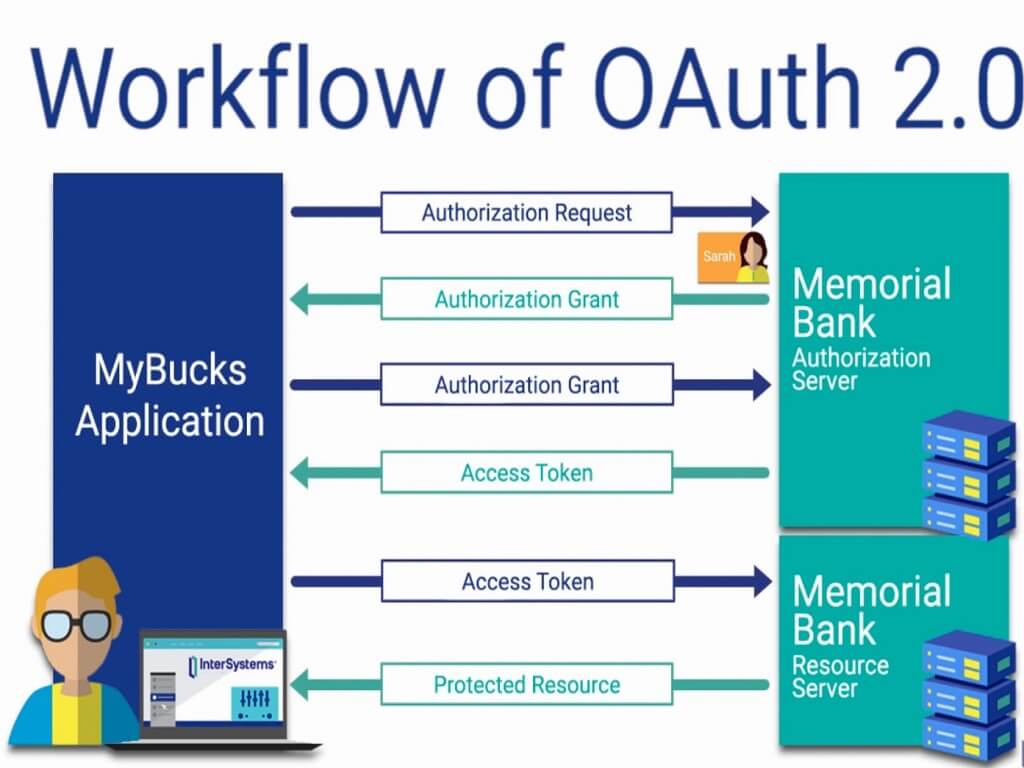
Generally, OAuth provides to clients a "secure delegated access" to server resources on behalf of a resource owner. It specifies a process for resource owners to authorize third-party access to their server resources without sharing their credentials. Designed specifically to work with Hyper Text Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access the protected resources hosted by the resource server.
OAuth is a service that is complementary to and distinct from OpenID. OAuth is unrelated to OATH, which is a reference architecture for authentication, not a standard for authorization. However, OAuth is directly related to OpenID Connect (OIDC) since OIDC is an authentication layer built on top of OAuth 2.0.
Security
OAuth 1.0
A session fixation security flaw in the 1.0 protocol was announced. It affects the OAuth authorization flow (also known as "3-legged OAuth") in OAuth Core 1.0 Section 6. Version 1.0a of the OAuth Core protocol was issued to address this issue.
OAuth 2.0
The Internet Engineering Task Force published a threat model for OAuth 2.0. Among the threats outlined is one called "Open Redirector"; in the year of 2014, a variant of this was described under the name "Covert Redirect" by Wang Jing.
OAuth 2.0 has been analyzed using formal web protocol analysis. This analysis revealed that in setups with multiple authorization servers, one of which is behaving maliciously, clients can become confused about the authorization server to use and may forward secrets to the malicious authorization server (AS Mix-Up Attack).This prompted the creation of a new best current practice internet draft that sets out to define a new security standard for OAuth 2.0. Assuming a fix against the AS Mix-Up Attack in place, the security of OAuth 2.0 has been proven under strong attacker models using formal analysis.
Implementations of OAuth 2.0 have had numerous security flaws exposed.
Attacks
Now, I’m going to talk about various attacks possible by modifying the requests.
- Attacking ‘Connect’ request
- Attacking ‘redirect_uri’
- CSRF on Authorization response
- Reusing an access token – One access_token to rule them all
- Open Redirect in OAuth 2.0
- Lack of Data confidentiality and server Trust
- Insecure storage of secrets
- HTTP 307 URL redirection
- Identity Provider (IDP) Mix up etc ...