Introduction
A Rainbow Table Attack is a password-cracking technique that uses a rainbow table to crack password hashes in a database. Cybercriminals used rainbow table compilation as an easy way to crack passwords to allow unauthorized access to systems. It does not rely on dictionary attacks (which consume more memory) or brute force attacks (which consume more processing power). All the attacker has to do is check the rainbow table to find the hash of the password.
What is Hashing?
A mapping approach is hashing. It employs a function to change one set of bytes into another set of bytes. The data that the hash function receives could be of different lengths. But the hash function's output, also known as the hash code or digest, is always the same length.
The fact that a hash function is a one-way function is important to remember. As a result, given only a hash code, it is impossible to retrieve the original plaintext input. There is a limited amount of hash codes, which is a feature of hashing. The size of the hash codes determines this quantity.
What is Rainbow Table?
A Rainbow Table is a set of pre-computed passwords and their corresponding hashes that can be used to find out what plaintext password matches a particular hash. The Rainbow Table is intentionally designed to use less processing power at the expense of more space. As a result, it usually returns results faster than a dictionary or brute force attacks, often taking minutes to crack when other methods take much longer.
Types of Rainbow Table Attack
The main function behind rainbow tables is the ability to perform cryptanalysis, also known as cryptographic algorithms, quickly and effectively. The most common types are:
- Direct mapping:In this method, the hash function maps the hash of the plaintext, so you cannot find the plaintext from the original hash.
- Reduced Mapping: Using this technique, you can ask for the hash of a plaintext but won't receive the actual plain text in return.
- Crossway Mapping: In this technique, chains in a rainbow table begin with a random plain text, hash it, and then reduce the hash to a different plain text. The starting plain text and the ultimate hash finish with millions of hashes are both stored in the Rainbow Table.
How does Rainbow Table Attack work?

Before a rainbow table attack can take place, an attacker must first have access to the leaked hash. For example, an attacker could find vulnerabilities in Active Directory or her corporate web application that uses a poorly secured password database. An attacker can steal a password hash and use a rainbow table to decrypt the passwords of all users of a system or application into plaintext passwords.
Let's say he has 1500 passwords to crack. A brute force attack would have to do this for each password by computing all possible word combinations and comparing them to the hash of the password. In Rainbow Table Attack, she calculated every hash once, and now all she has to do is find the correct hash.
In addition to these techniques, criminals have access to millions of leaked password hashes on the dark web. Once you have these password dumps, rainbow tables can help you crack password hashes. So, this is how the Rainbow Table Attack works.
Rainbow table attack demo
Step 1: Install the rainbow crack first.
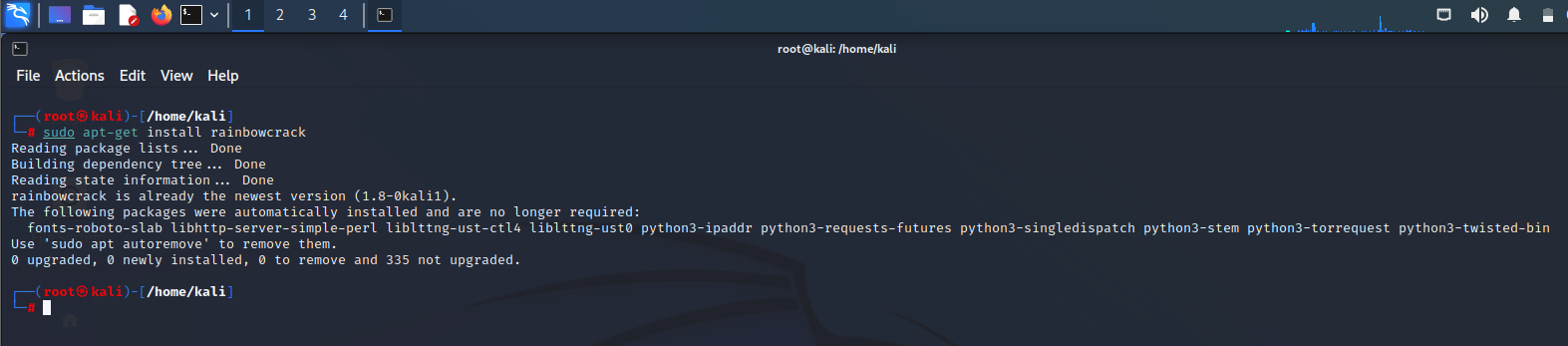
Step 2: Use rtgen to see the syntax and to see whether rainbow crack have been installed.
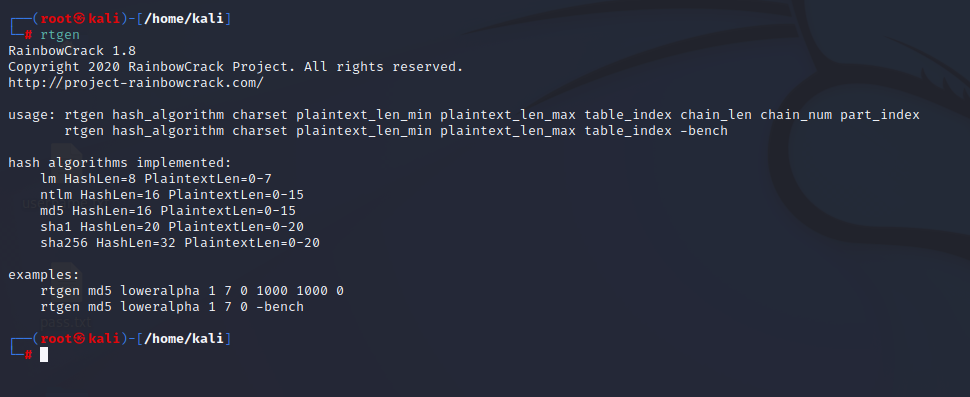
Step 3: Use the highlighted command to create a rainbow table or you can modify it according to your wish with same syntax.
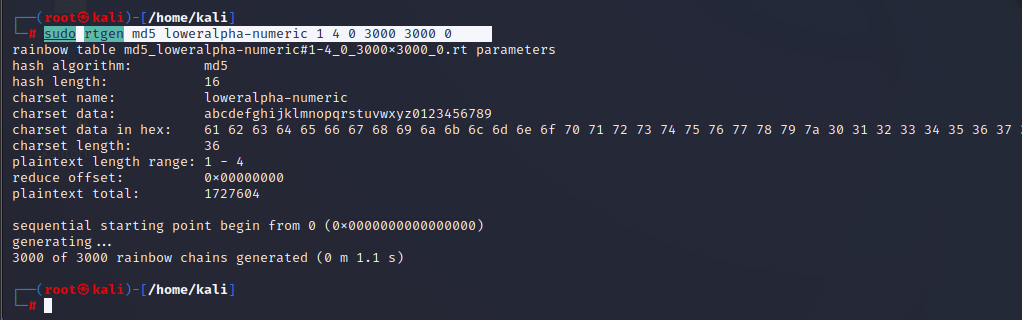
Explanation:
rtgen – rainbow table generations
md5 - hash_algorithm
Loweralpha-numeric - charset
1 - plaintext_len_min
4 - plaintext_len_max
0 - table_index
3000 - chain_len
3000 - chain_num
0 - Part_index
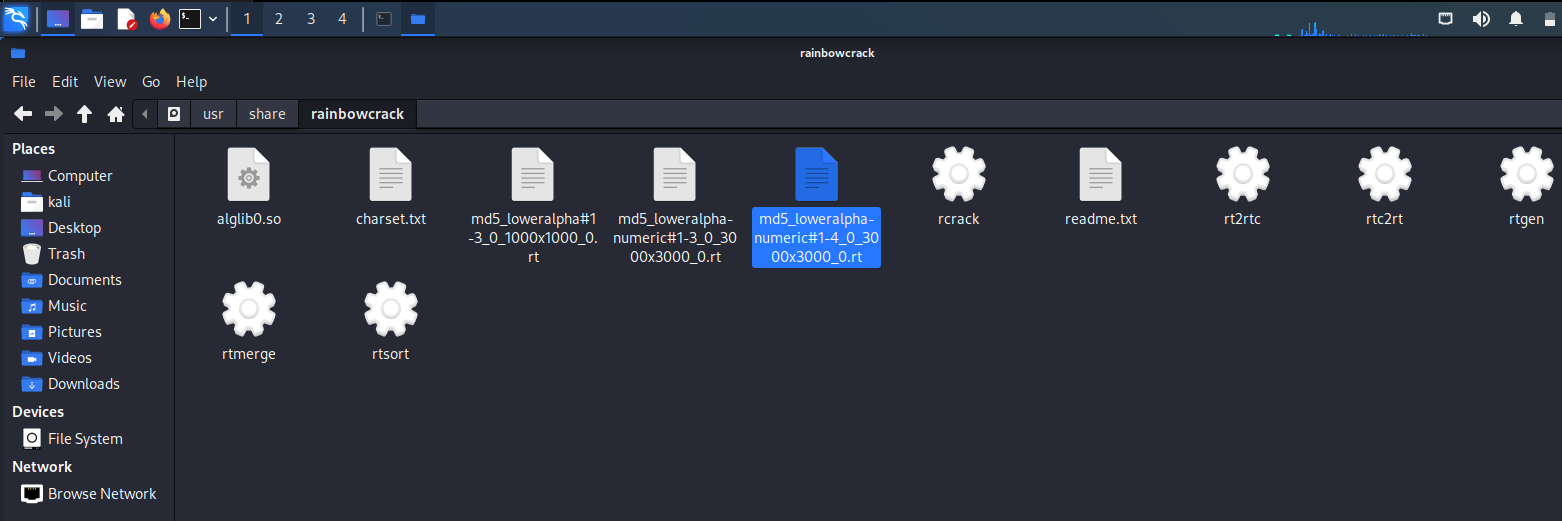
Step 4: After creating the rainbow table, you can view the rainbow table form the following path: File system > usr > share > rainbowcrack
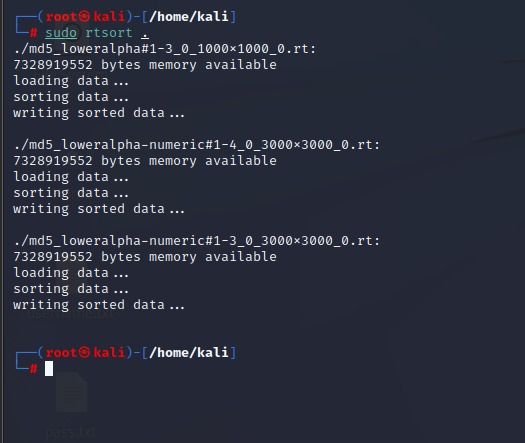
Step 5: Use sudo rtsort to check all the rainbow table present in your system.
Step 6: use rcrack to see the password for the hash code given.
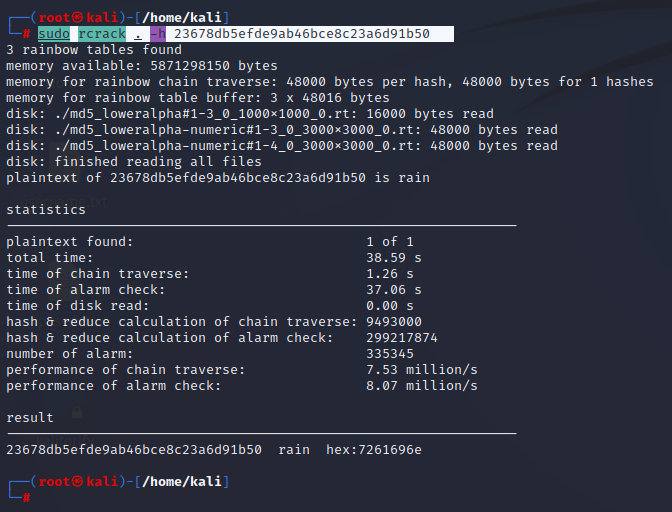
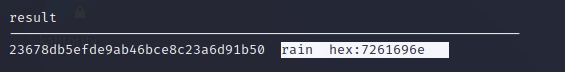
Step 7: The result will show the cracked password as below.
How to prevent Rainbow Table Attacks?
Defending your system or application against rainbow table attacks is relatively straightforward. You can use the following simple steps:
- Password salting: The main defense against rainbow table attacks is password salting. Salt is a simple way to introduce randomness into the resulting hash. Salts allow passwords to be hashed in multiple ways. Without salt, the same password will have the same hash every time. Therefore, hashed passwords should never be stored without salt. Instead of creating one rainbow table for the unsalted system, the salted system would require thousands or more rainbow tables depending on the length of the salt. This makes passwords harder to crack.
- MFA: Multi-factor authentication (MFA) or two-factor authentication (2FA) allows someone to access your account using something like your identity (biometrics) or something you have (tokens) becomes difficult. password. This prevents the attacker from using Rainbow his table attack effectively.
- Avoid outdated hashing algorithms:Attackers are looking for applications and servers that use outdated password hashing algorithms such as MD5 and SHA1. Or hash without salt. In particular, Windows LM and NT hashes do not contain salts, making them particularly vulnerable to rainbow attacks. Using these vulnerable algorithms in your applications greatly increases the risk of rainbow table attacks.
- No passwords:Without a password hash to steal, a rainbow attack wouldn't happen at all. Unfortunately, users always find ways to use weak passwords. They struggle to remember strong passwords and end up writing them down to reuse. Weak passwords are easy to crack, leaving businesses vulnerable to data breaches. Going without a password is a surefire way to eliminate the threat of rainbow attacks.
Are rainbow Table Attacks still a threat?
Some security experts claim that the latest password-cracking techniques have made rainbow tables obsolete. Instead, most attackers now use more sophisticated password-cracking techniques based on graphics processing units (GPUs).
A medium-sized GPU farm can easily rebuild a rainbow table in seconds. This means that encoding these passwords into a rainbow table doesn't make much sense. Also, most passwords are salted anyway. This means that you need a rainbow table for each salt value, and for larger salts, this is completely impractical. Bitcoin and other cryptocurrency miners utilize GPU technology to calculate hashes for Bitcoin farming. There are existing tools that may be able to crack password hashes using GPU technology.
Illustration of Rainbow Table Attacks
- Attackers find web applications with outdated password hashing techniques and poor overall security. An attacker steals password hashes and uses the Rainbow table to crack passwords for all users of the application.
- Hackers find vulnerabilities in corporate Active Directory and gain access to password hashes. Once we have the list of hashes, we perform a rainbow table attack to decrypt the hashes into plaintext passwords.
Conclusion
Rainbow table attacks are used by hackers today due to their main advantage of being a very fast password-cracking technique. In a short period, security scientists have tackled this hacking activity and developed sophisticated techniques to solve it. The best known are 'salt' and 'key stretch'.