This is Part 2 on thick client applications, basics of thick client applications have been covered in Introduction to thick client applications.
As per OWASP Windows Binary Executable Files Security Checks Project, thick client penetration testing involves a series of tests in order to conduct successful penetration testing.
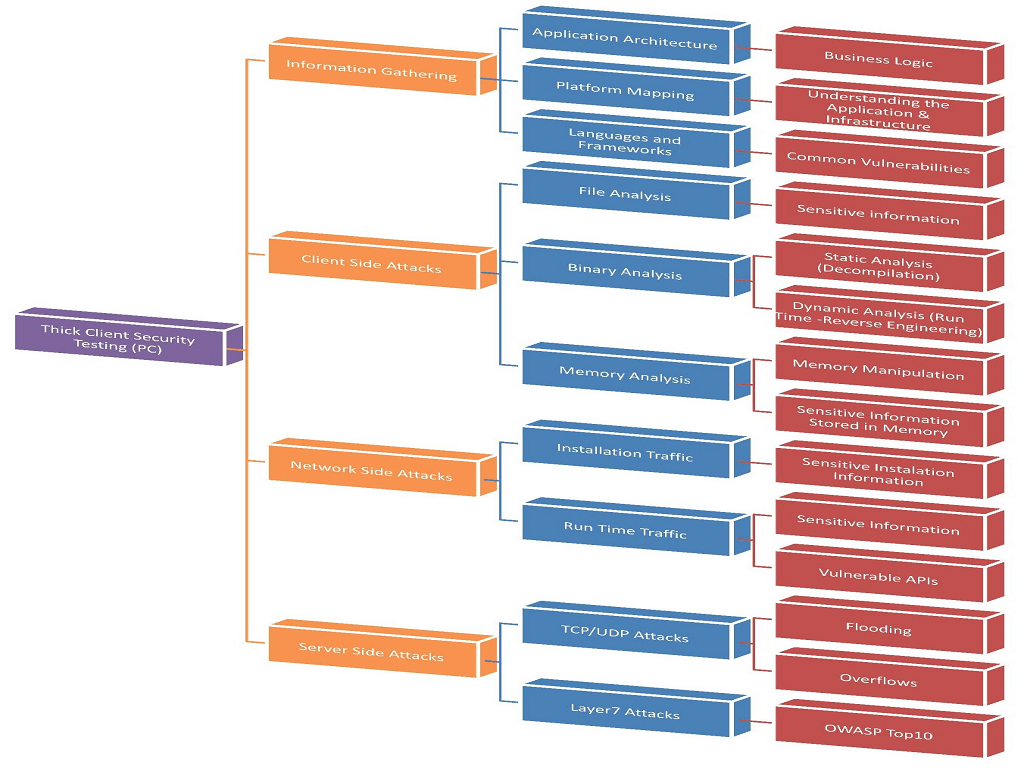
Information Gathering
This phase involves identifying the languages and frameworks used by the application and drawing a complete architecture of an application. This is necessary in order to understand the full functionality of the thick client application.
We should understand the privileges and roles of every type of user in the application. For Example, Administrators and Users usually have different functionality and level of access.
We can use various tools to get to know the languages used by the thick client applications, they are:
| Tool Name | Description |
|---|---|
| Detect It Easy (DIE) | A program for determining file types for Windows, Linux and macOS |
| Strings | It scans any files you pass it for UNICODE or ASCII strings of a default length of three or more UNICODE or ASCII characters. |
| PEid | This tool detects most common packers, cryptors and compilers for PE files. |
| CFF Explorer | This tool was designed to make PE editing as easy as possible without losing sight of the portable executable’s internal structure. |
Static Tools used for Information gathering
I loaded DVTA application into CFF Explorer to understand the application’s internals, For example, the framework and file type. Here the application is built using .NET.
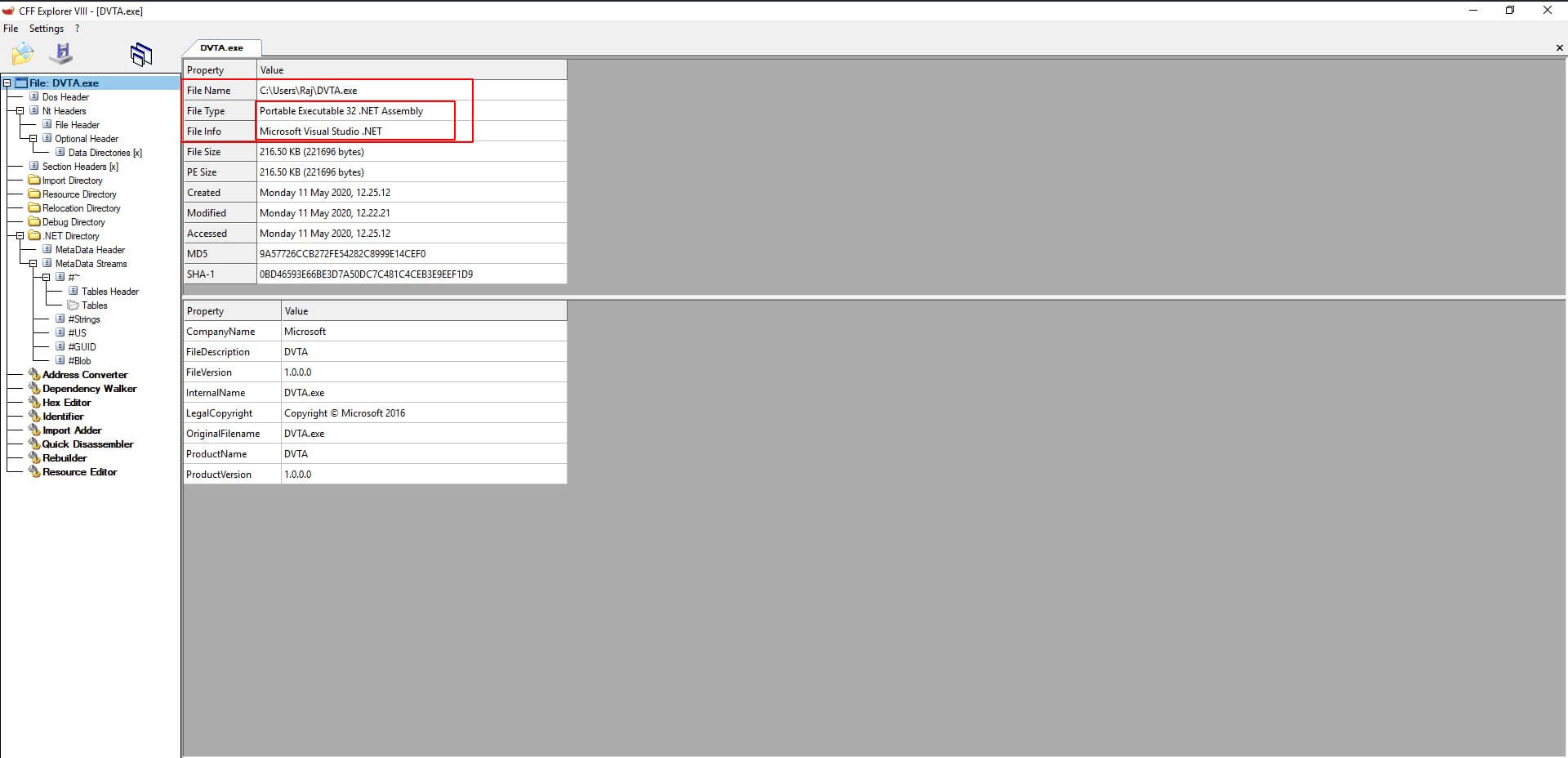
Then we can use various decompilers and deobfuscators to retrieve the source code for further analysis.
Some of the .NET decompilers are mentioned below:
| Tool Name | Description |
|---|---|
| dnSpy | A .NET debugger and assembly editor. |
| JetBrains DotPeek | .NET program to determine types of files for Windows, Linux, and macOS. |
| ILSpy | ILSpy is the open-source .NET assembly browser and decompiler. |
In the next phase, we will determine the Network Communication Between the Application Client and the Server
We can use tools like Wireshark, tcpdump or any network packet sniffing tool of your choice to find out the protocols and analyse the network traffic of a given application.
Wireshark and other network sniffing tools will help us to identify how the application communicates with the server and whether the sensitive data such as credentials or API keys are sent to the server in plaintext.
Using packet sniffing tools, we should look how the data is being transmitted to the server. The sensitive data should be transferred in an encrypted manner over the network, we should look for data such as:
- HTTP and HTTPS web endpoints (Web Services, REST API)
- Sensitive data transferred over an unencrypted tunnel (clear-text credentials/secrets/API Keys etc.)
- Company owned Private protocols (aka Proprietary protocols) used by the program
- File blobs/chunks sent over the wire
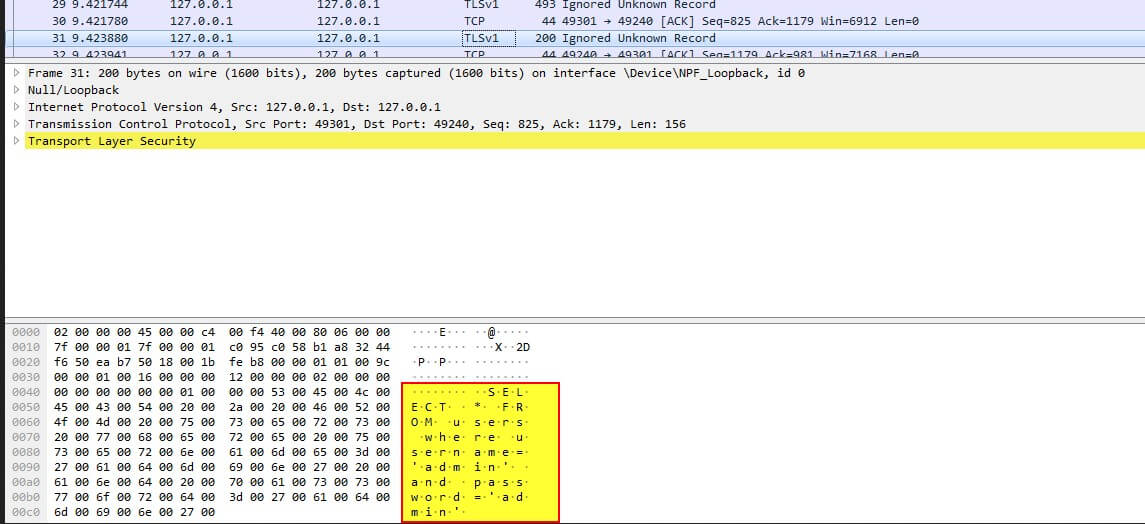
Packet sniffing using Wireshark
After setting up the DVTA app, Run Wireshark and then enter the credentials, In Wireshark we can see that the .NET application is transmitting credentials in clear text.
Until now we have used only network sniffers, now we need to intercept the thick client traffic using Network Proxies such as Burp Suite and Echo Mirage.
There are two types of thick client applications:
- Non-proxy-aware – A thick client that does not have any settings options in the application itself and requires a different testing approach. For these applications we need to use tools such as Burp suite to connect to a Proxy listener and then intercept the traffic.
- Proxy aware – A thick client that has settings options in the application itself. In these applications it may be possible to intercept the traffic using any proxy tool.
Below figure shows how to use Burp suite to intercept the traffic in non-proxy aware applications, in Burp Suite, Go to Proxy -> Options -> Add -> Click on Request Handling -> Enter the host ip address and port number and Enable Support invisible proxying.
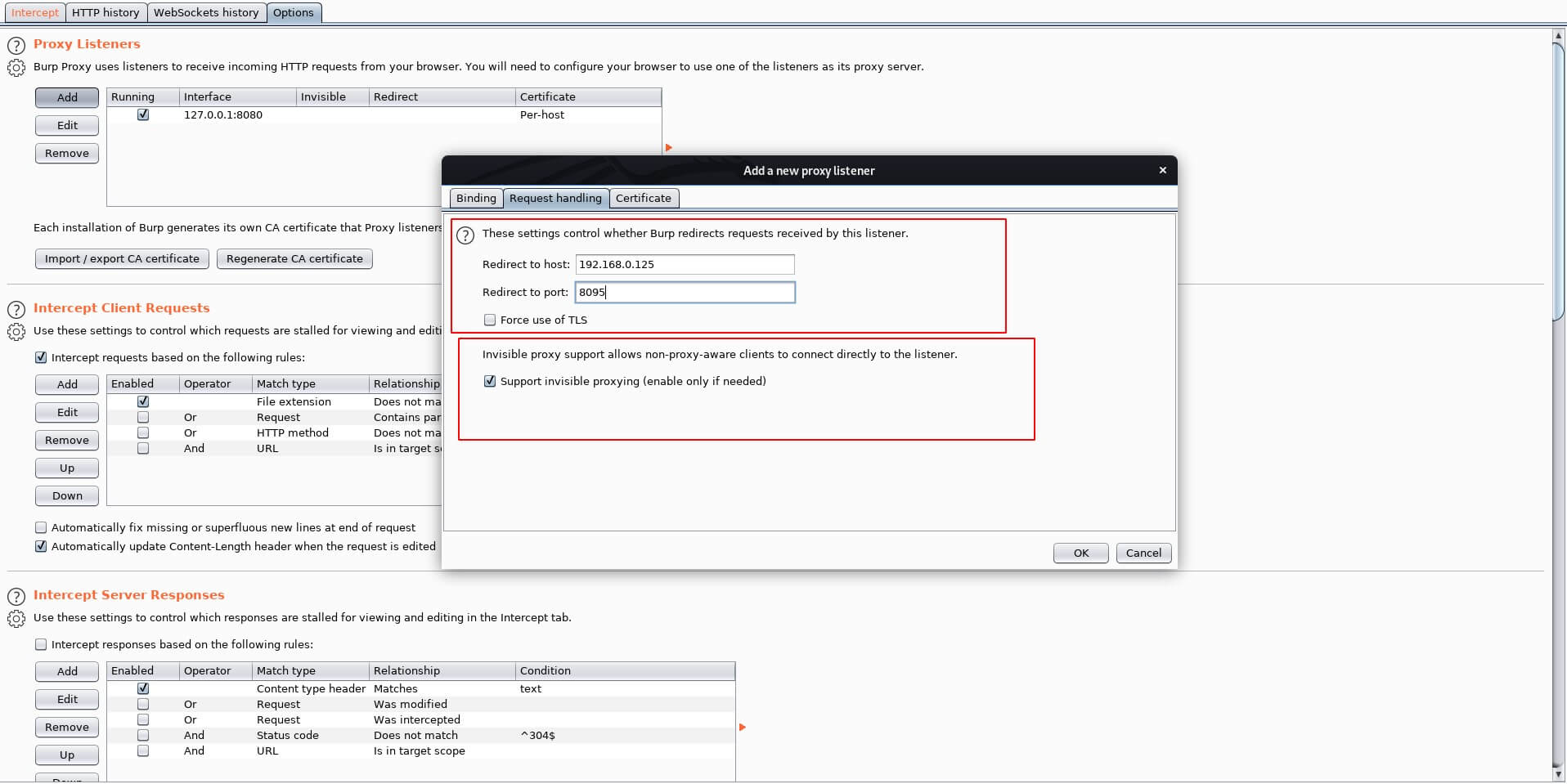
Using these proxy tools, we can intercept the client traffic and modify the requests before being sent to servers. Tools like Echo mirage will help to inject into the client application and then modify the SQL queries.
In the next part we will look at Client-side attacks and server-side attacks.





