The Trojan — affecting mostly users in India, the US, and Russia — has since shot up to the top 10 list of most detected mobile malware, with security researchers observing what they call “a surge in detections” of the malicious Android malware that can hide itself from users, download additional malicious apps, and display advertisements.
“In the past month alone, there was an average of 131 devices infected each day, and an average of 2,400 devices persistently infected throughout the month,” It’s pegged the number of affected phones at 33,000, suggesting a rapid increase in just over two months.
Origin:
While the exact origins of xHelper is being actively investigated, researchers suspect two different possibilities: a rogue app laced with the malware is possibly being downloaded by users from unknown sources, or a malicious system app that’s persistently downloading the malware despite users performing factory resets and manually uninstalling it.
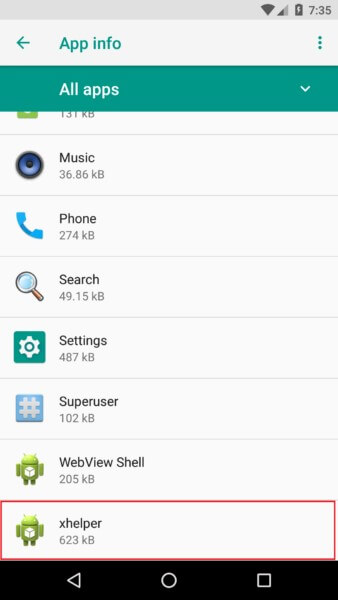
Aside from operating silently in the background, xHelper takes its stealth behaviour to new heights by not creating an app icon or a shortcut icon on the home screen launcher. The only indicator is a listing in the app info section of the infected phone’s settings.
The lack of an app icon means the malware cannot be launched manually. But to get around the problem, it relies on external triggers — like connecting or disconnecting the infected device from a power supply, rebooting a device, or installing or uninstalling an app — to run itself as a foreground service that minimizes the chance of getting killed.
Name stealer:
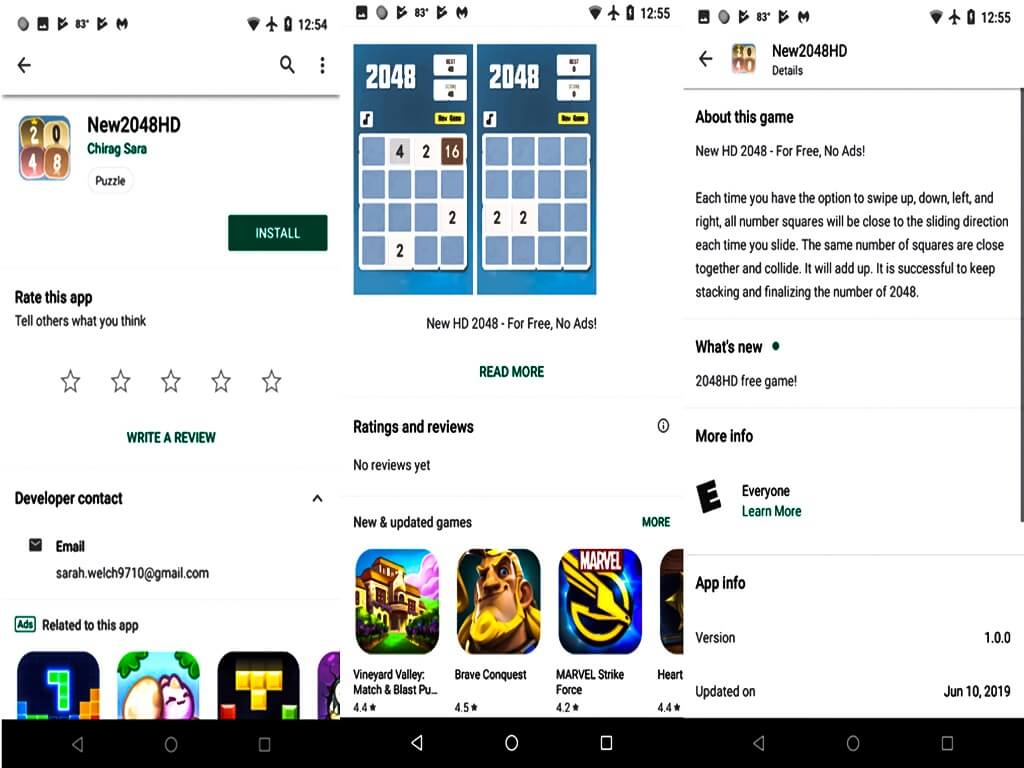
The first noticeable characteristic of xHelper is the use of stolen package names. It isn’t unusual for mobile malware to use the same package name of other legitimate apps. After all, the definition of a Trojan as it relates to mobile malware is pretending to be a legitimate app. However, the package names this Trojan has chosen is unusual.
o demonstrate, xHelper uses package names starting with “com.muf.” This package name is associated with a number of puzzle games found on Google Play, including a puzzle called New2048HD with the package name com.mufc.fireuvw. This simple game only had a little more than 10 installs at the time of this writing. Why this mobile malware is ripping off package names from such low-profile Android apps is a puzzle in itself. In contrast, most mobile Trojans rip off highly-popular package names.
Full-stealth vs semi-stealth
xHelper comes in two variants: full-stealth and semi-stealth. The semi-stealth version is a bit more intriguing, so we’ll start with this one. On install, the behaviours is as follows:
- Creates an icon in notifications titled “xhelper”
- Does not create an app icon or a shortcut icon
- After a couple of minutes, starts adding more icons to notifications: [Game centre] Free Game
- Press on either of these notifications, and it directs you to a website that allows you to play games directly via browser.
- These websites seem harmless, but surely the malware authors are collecting pay-for-click profit on each redirect.
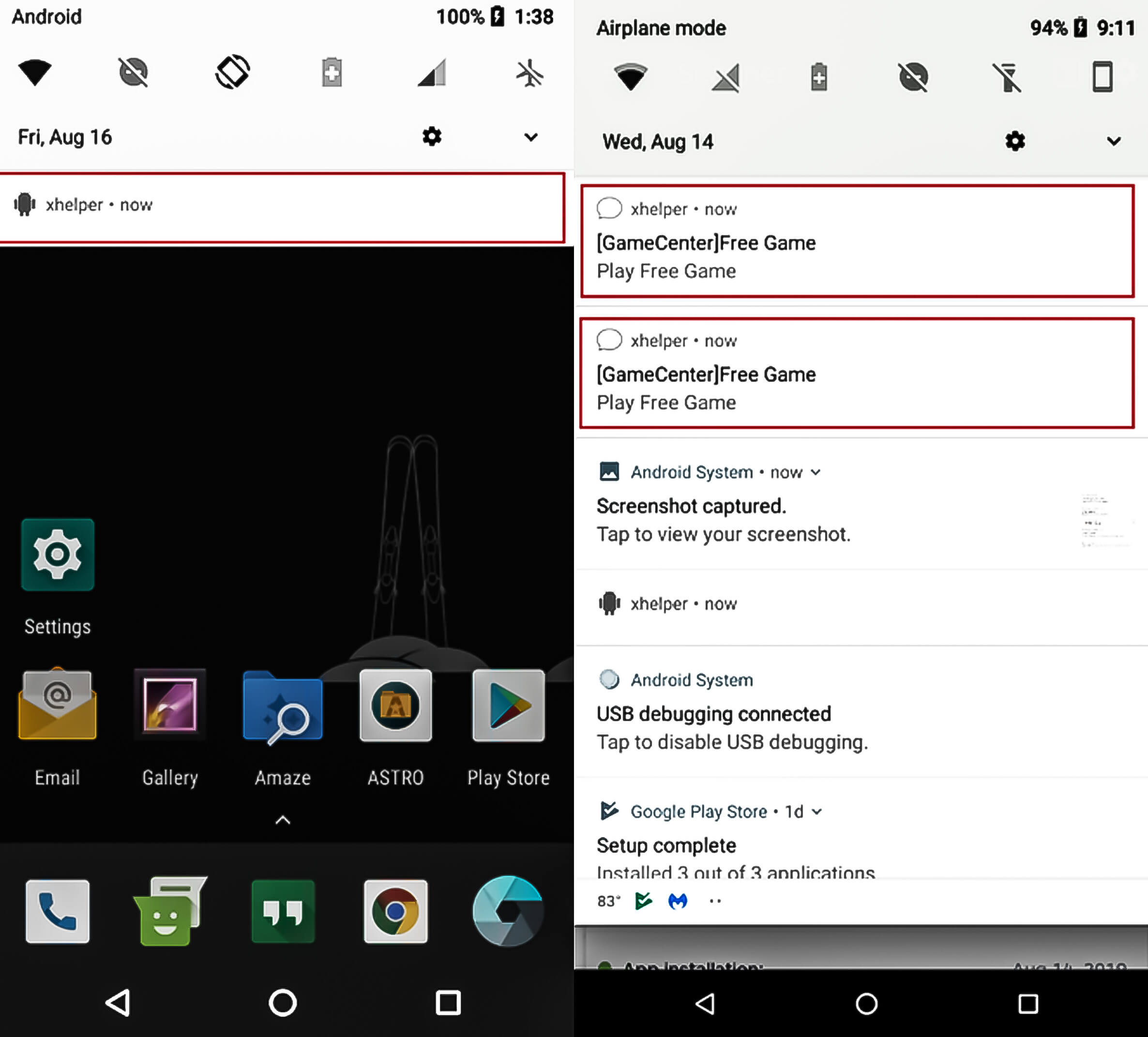
The full-stealth version also avoids creating an app icon or shortcut icon, but it hides almost all traces of its existence otherwise. There are no icons created in notifications. The only evidence of its presence is a simple xhelper listing in the app info section.
The big question: What is the source of infection that is making this Trojan so prominent? Obviously, this type of traffic wouldn’t come from carelessly installing third-party apps alone. Conclude that this mobile infection is being spread by web redirects, perhaps via the game websites mentioned above, which are hosted in the US as well, or other shady websites.





