Insecure data storage vulnerabilities occur when application store sensitive information such as username, password, and credit cards numbers in plain text. For storing this kind of data, we need a strong security mechanism. Sometimes developers use databases or saved settings to store these kinds of data in web and server-based application however in mobile application it will not work always. The developers assume that the users or malware will not have access to mobile devices filesystem and sensitive information in the device, but file system is easily accessible. The developers should expect a malicious user or malware to inspect sensitive data. Don’t use any insecure encryption mechanism because jailbreaking or rooting a mobile device will bypass its protection. When data is not protected properly there are many tools that is used to view the application data.
Impact
Insecure data storage can result in data loss. at most, for an individual user. The important valuable data which are frequently stored:
- Usernames
- Authentication tokens
- Passwords
- Cookies
- Location Data
- Personal data: DoB, credit card etc.
Demo
For demo purpose we are using Damn insecure vulnerable application (DIVA). You can download the application from here: -https://github.com/payatu/diva-android
Insecure data storage - Part 1
Step 1: To see how the application stores data, we need to decompile the application. To decompile the application, you can use jadx
To download jadx- https://github.com/skylot/jadx
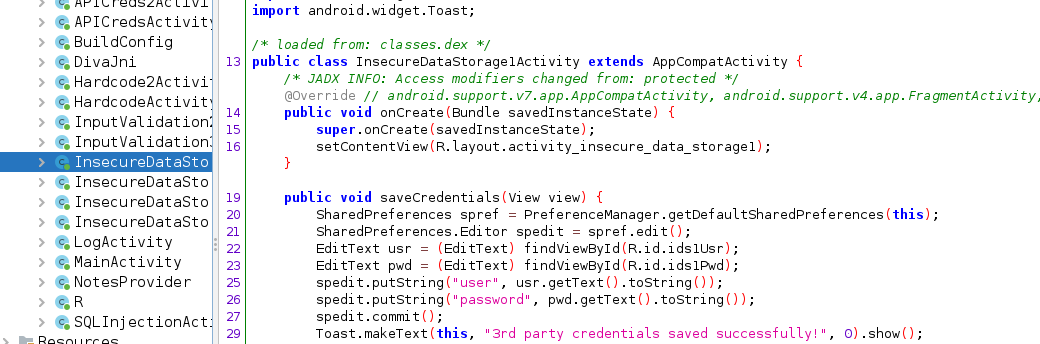
From the above code we understand that diva uses preferenceManager to store plaintext data.PreferenceManager saves data in XML in application path.
Step 2: Enter some random data
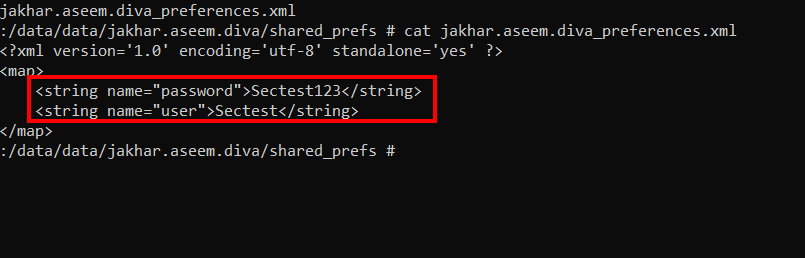
Step 3: Any application which has root access can read that sensitive information. To see sensitive information, move to
data/data/jakhar.aseem.diva/shared_prefs/jakhar.aseem.diva_prefernces.xml
Recommendation
Use the EncryptedSharedPreferences API or other encryption algorithms for storing sensitive information.
Insecure data storage part 2
Step 1: Decompile the application using jadx
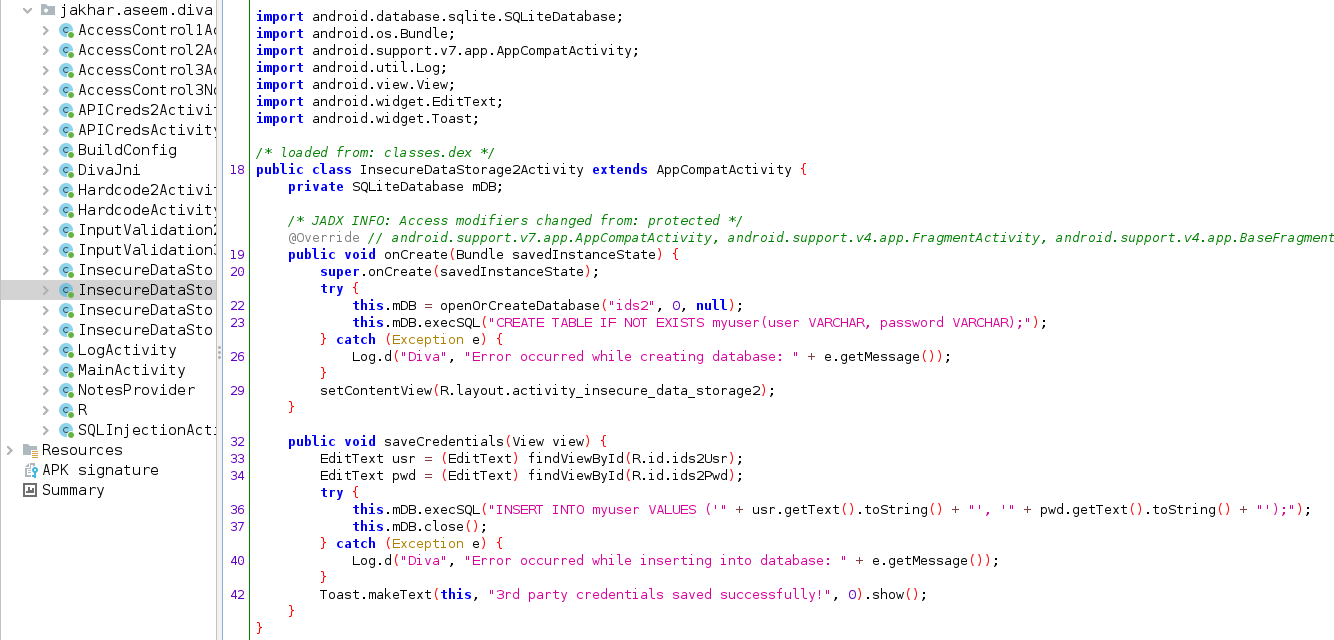
The DIVA application is storing the sensitive details in database file. That means we can find the credentials from the application folder
Step 2: Enter the credentials
Step 3: To read the file from databases move to application filesystem
data/data/jakhar.aseem.diva/databases
You can use SQLite to read dB file
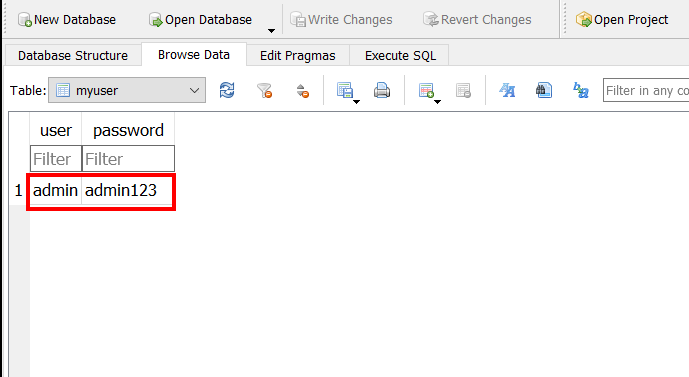
From the database file we can see that credentials are stored in plaintext.
Recommendation
Use SQLCipher or similar libraries to add encryption capabilities to SQLite or encrypt the sensitive data using cryptographically secure algorithms before storing it in the database.
Insecure data storage - Part 3
Step 1: Decompile the application
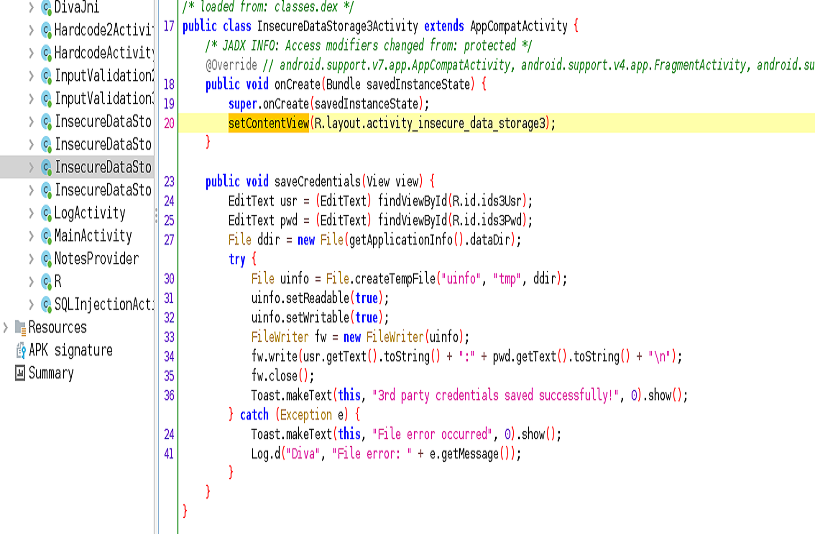
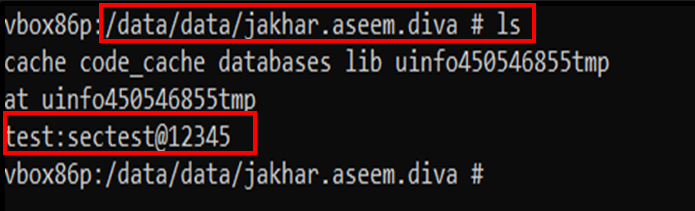
From the above code we understand that DIVA application is storing the credentials in a temporary file which is created by application in the data directory.
Step 2: Enter some random data to see how the application store the sensitive data
Step 3: Read the file
Recommendation
Use hashing algorithms like MD5 or SHA1 to prevent storing plain text data.