
Phishing : The Rising Threat To Business
Phishing is a technique in which an attacker sends an email or provides a link falsely claiming to be from a legitimate site to acquire a user’s personal or account information. The attacker registers a fake domain name, builds a lookalike website, and then mails the fake website’s link to users. When a user clicks on the email link, it redirects them to the fake webpage, where they are lured into sharing sensitive details such as their address and credit card information. Some of the reasons behind the success of phishing scams include users’ lack of knowledge, being visually deceived, and not paying attention to security indicator.
Cyber criminals use phishing emails because it’s easy, cheap and effective. Email addresses are easy to obtain, and emails are virtually free to send. With little effort and little cost, attackers can quickly gain access to valuable data. Those who fall for phishing scams may end up with malware infections (including ransomware), identity theft, and data loss.
Why Arridae?
- A dedicated industry certified collaborative team with experience and expertise produces the highest quality of work.
- Focused more into manual testing over automated testing to avoid false positives.
- We assure you high quality testing on time and every time.
-
What is Phishing Simulation and Why it is Important?
Phishing Simulation means that you will be phishing your own team to test the effectiveness of your phishing training. The simulated phishing emails may look like they are from a manager, vendor, or a well-known brand name. The idea is to find out how good people are at identifying these emails as fake and reporting them. Those who fail the phishing test usually get an explanation of what they can do next time to spot these phishing emails better.
Why are phishing simulations important ?
- It's an effective way to determine how likely your employees will click on real phishing emails by simulating a phishing attack.
- To ensure people know how to report a phishing attack, for example, by clicking on the “Report Phishing Button” or notifying the Security Team. You don't want people to forward phishing emails to their friends because this may cause even bigger problems. You also want to determine how many people report these phishing emails vs. doing nothing. The more people report the phishing test, the better.
- It's a great way to test the security team's resilience to phishing attacks. What do they do with phishing emails people report? Does the security team follow the playbook? Do they follow up with the people who reported or do nothing?
-
Impact on Phishing
Loss of Money
From every phishing incident that has ever taken place in history, one constant effect is financial loss. First is the direct loss from transferred funds by employees who were fooled by the hackers. Second is the fines for non-compliance imposed by regulatory bodies like HIPAA, PCI, and PIPEDA,among others.
In the event of serious violations of data protection standards, these fines could go through the roof.
Finally, Finally, there are costs of investigating the breach and compensating the affected customers, which would further compound the company's financial losses.
Loss of Intellectual Property
Financial losses are not the only thing businesses have to worry about in the event of a phishing attack. Even more devastating is the loss of customer data, trade secrets, project research, and blueprints
When the company at stake is in the tech, pharmaceutical, or defense industries, a stolen patent would mean millions of research expenditures going down the drain
Damage of Reputation
Businesses often try to hide the fact that they have suffered any phishing attacks. The major reason for this is the damage to reputation. Customers often patronize brands they consider to be reliable and trustworthy. Not only will the disclosure of a breach taint the brand image, but it will also break that established trust. Regaining customers' confidence is no easy feat, and the value of a brand is directly related to its customer base.
-
Our Approach
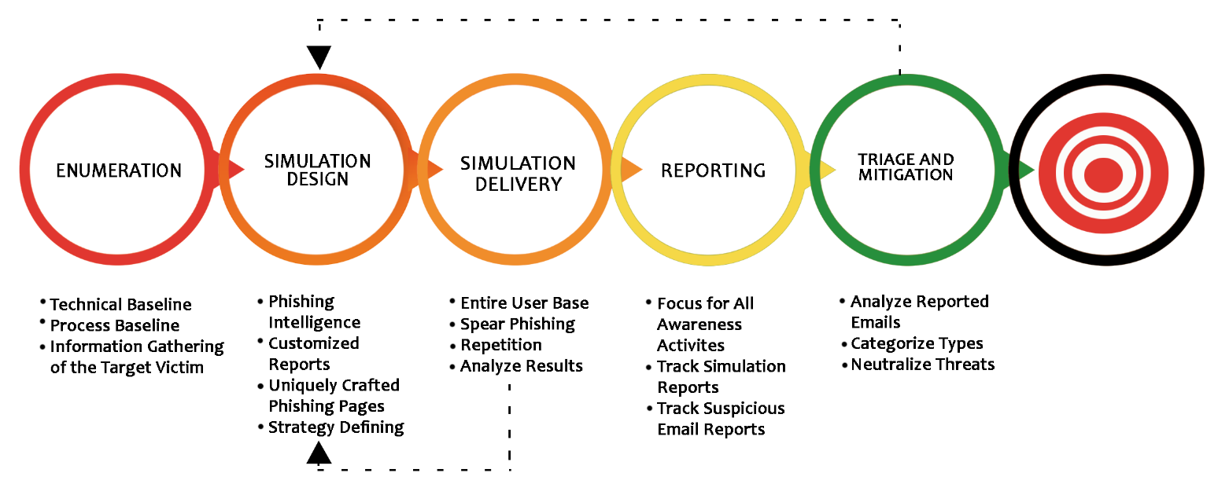
Methodology
The Arridae Team’s phishing simulation methodology combines industry-standard approaches with our knowledge to provide a tailored approach to testing employees' compliance with corporate rules and their capacity to protect company assets.
- Recon and Information Gathering:- Information gathering in an email phishing test will include obtaining staff email addresses and names, as well as learning information about the organisation that may be utilized to construct relevant pretexts for phishing emails.
- Attack Planning:- The data gathered in the previous steps is used to create a strategy. The story that will be utilized and who will be shown as the sender of the phishing email, the email content, the email addresses and names of targets, the engagement goals, timing, and so on are all elements of an email phishing engagement's plan of attack. Our staff will also work with the client contact to obtain approval for the content and format of the phishing emails.
- Execution:- This is where the operation is carried out, the email campaign is launched, and the results are tracked. Phishing emails are typically sent out in stages, spanning hours or days depending on the amount of employees targeted, and then the email campaign is left open/active for a week or two to allow for recipients who do not read their emails in a timely manner.
- Reporting:- The Report will be shared as per our format, which contains the detailed results of the phishing attack simulation including the table consisting of: Email Template Used, Total Emails Sent, Total Clicks, Unique User Clicks, User Clicks Rate, User Reported, User Reported Rate etc.
-
Deliverables
Comprehensive phishing simulation report consisting of Objectives, Executive Summary, implementation, result of phishing simulation and recommendations with prioritized action plan
