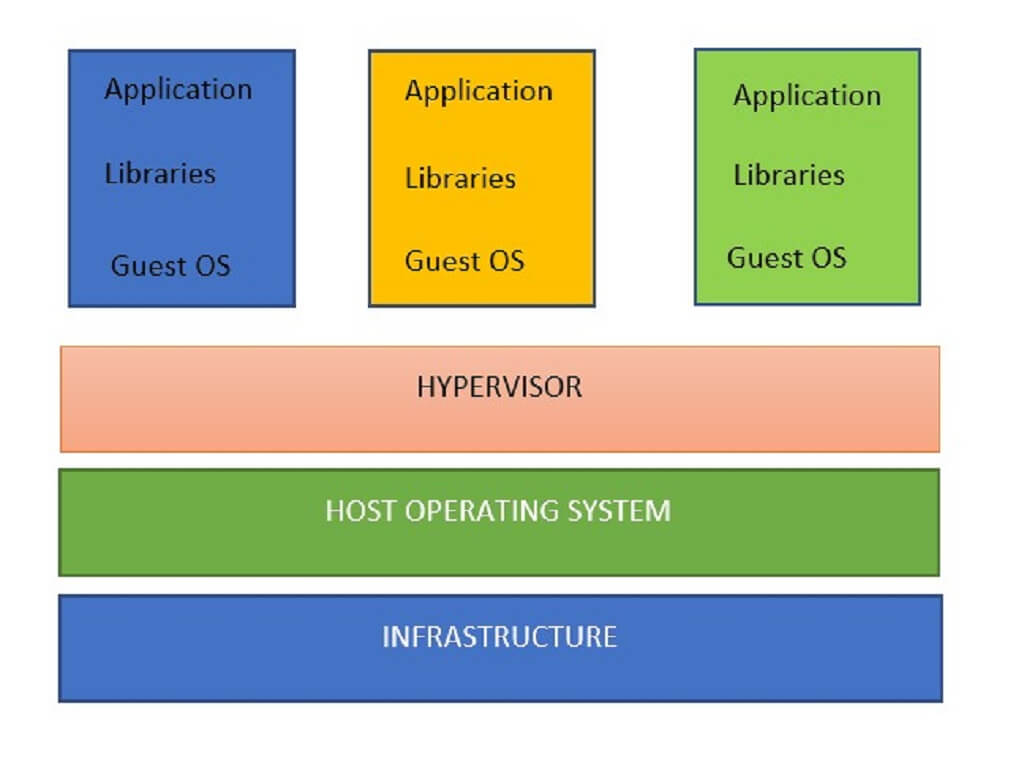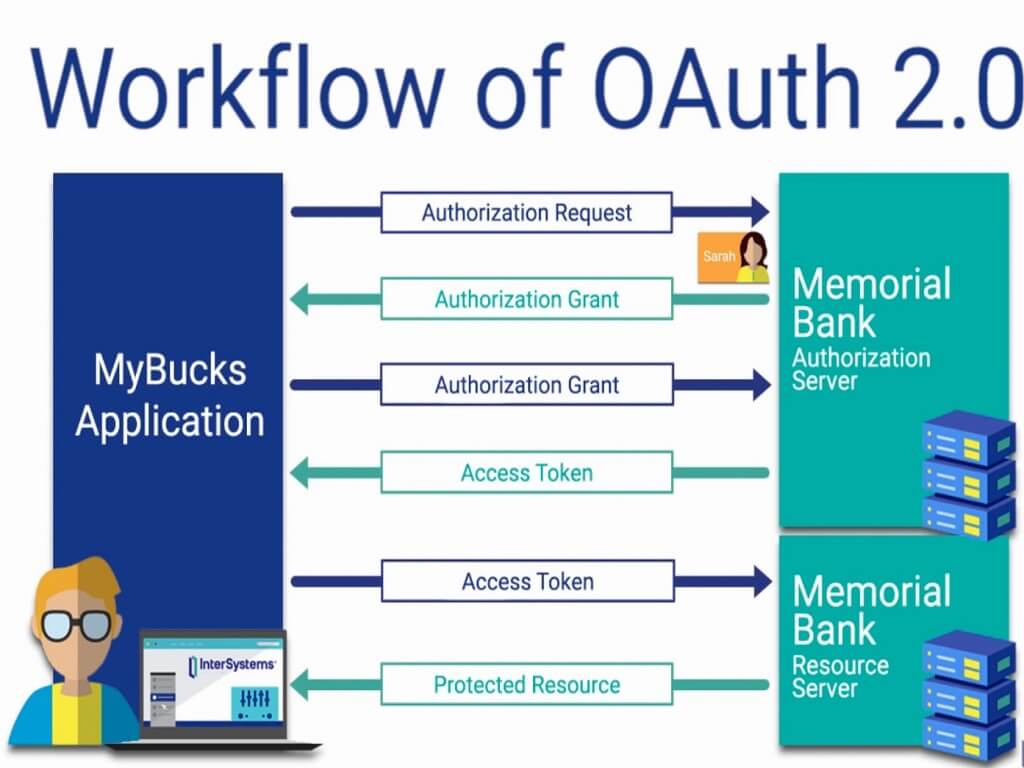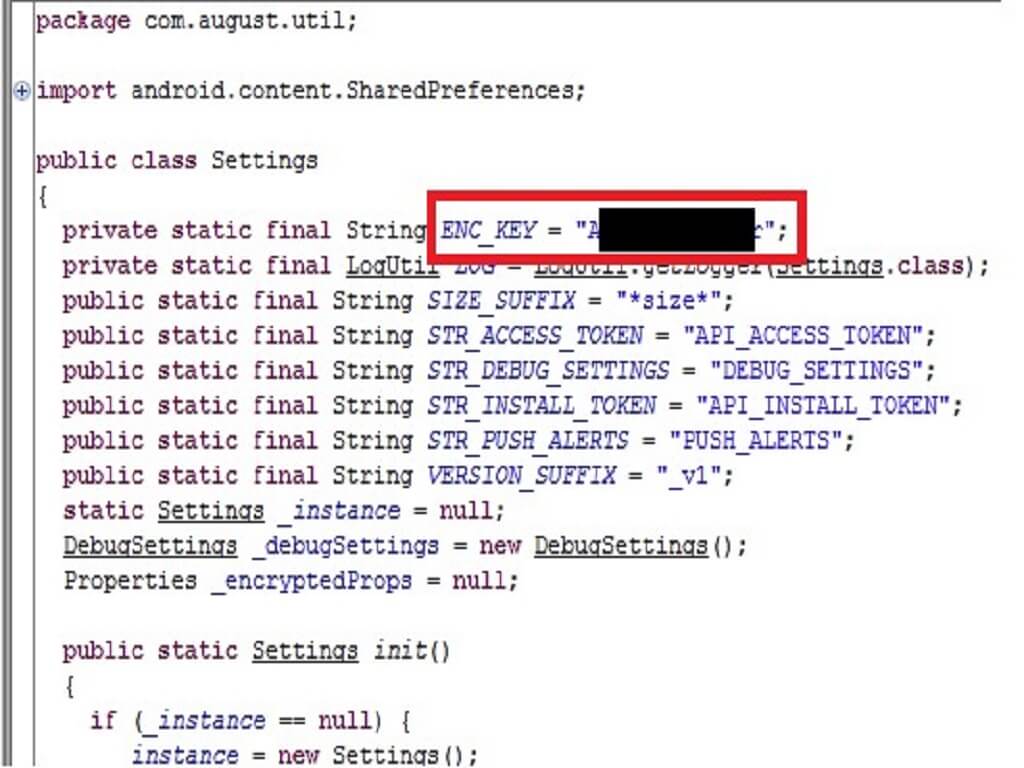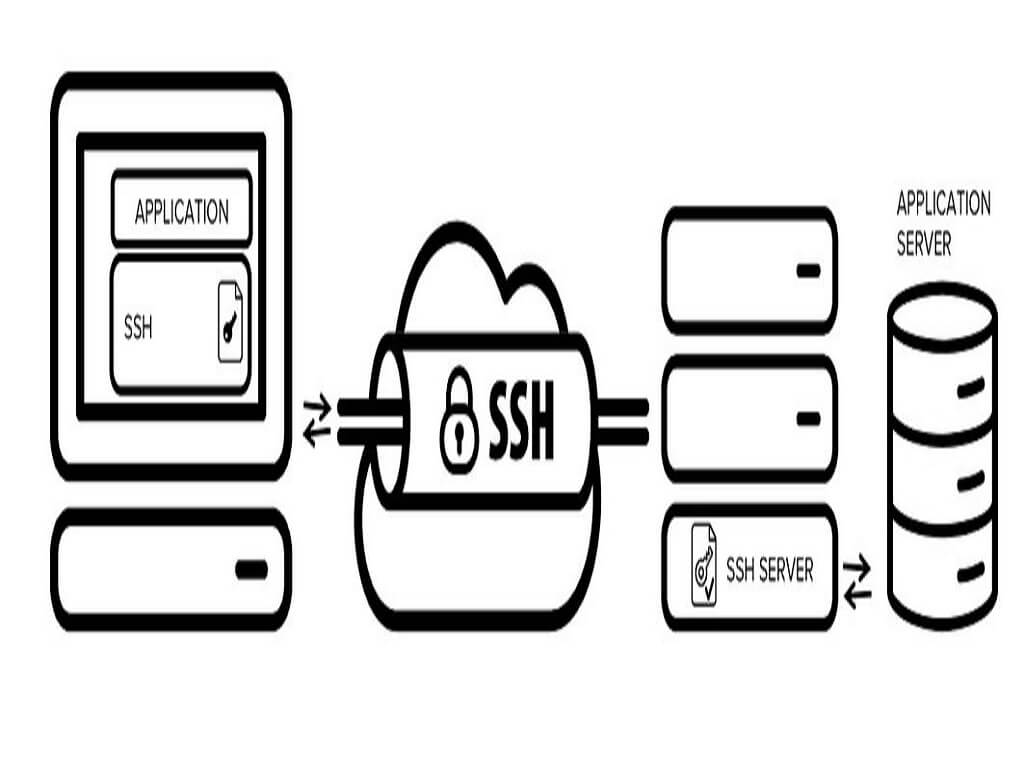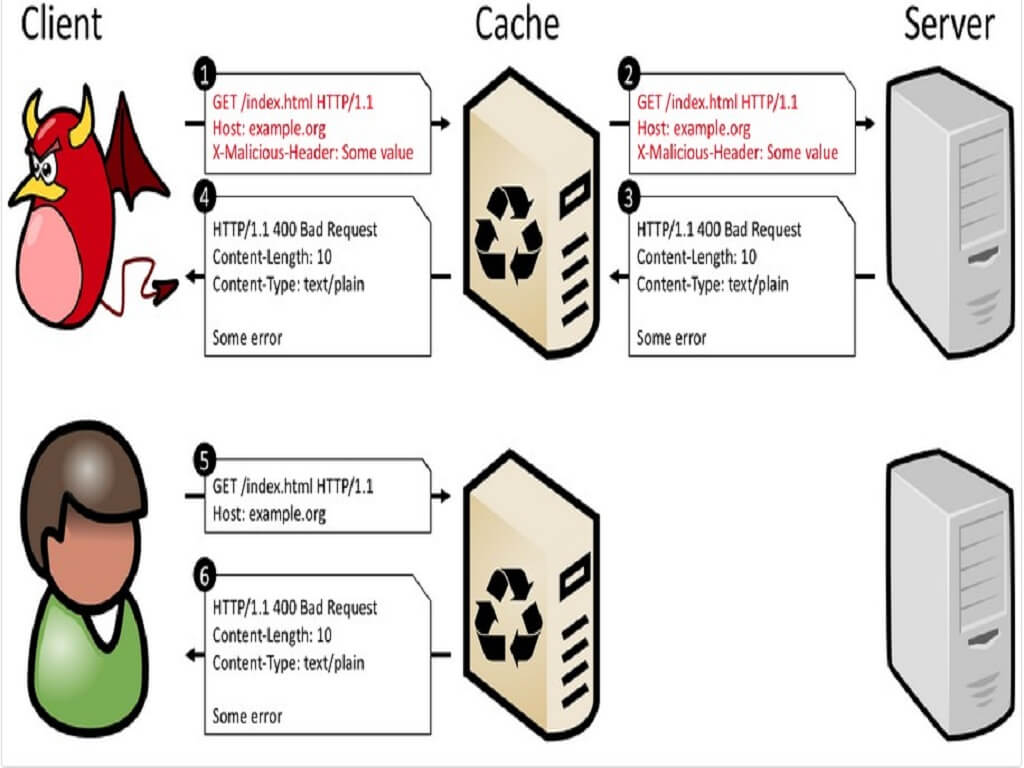
Cache-Poisoned Denial-of-Service Attacks
Security researchers found a new type of web attack last month named CPDoS (Cache-Poisoned Denial-of-Service), that can poison content delivery networks (CDNs) into caching and then serving error pages instead of legitimate websites.